By migrating to Fugue, enterprises, agencies, and DevSecOps teams in any organization centralize their control and visibility of systems running in the cloud, while accelerating secure deployments and updates. Human error—typical with scaled, enterprise infrastructure and costly in dollars and consumer trust—is drastically reduced since Fugue highlights mistakes and provides fixes before any provisioning occurs.
Because Fugue unifies policy-as-code and infrastructure-as-code upfront, you get blueprints that serve as a definitive source of truth for what’s running in a cloud environment, compliant across many accounts and projects. With design-time and runtime validations implemented, teams won’t provision infrastructure that violates a company’s rules. Fugue’s comprehensive governance goes further, uniquely asserting continuous, automated monitoring and runtime enforcement of your cloud blueprints.
Businesses eliminate policy infractions, infrastructure misconfigurations, drift, unapproved changes, and unknown state with Fugue. Serious technical concerns over resource dependencies and order of operations disappear. Your IT teams align to deliver product value to customers, instead of worrying about the heightened risk of misconfigured S3 buckets or the runaway costs of forgotten accounts and services.
New and Enhanced Capabilities
Easy migration of existing cloud workloads to Fugue.
Consider an enterprise that has a multitude of VPCs and other AWS services with complex configurations supporting vital, running systems. There’s no need to take down, recreate, or duplicate that infrastructure already in place or any selected part of it. It doesn’t matter how you provisioned resources, which marketplace tools you’ve used, which vendors you’ve tried. You can transition to Fugue and apply its robust governance to your running cloud resources in two easy steps. Begin either with Fugue’s Composer or its CLI to initiate the transcribing and import of your running AWS workloads, shown below in this blog. Within minutes Fugue governs imported resources, with no service interruptions and no downtime, delivering the same active state enforcement and policy compliance that it does for resources initially created with Fugue.
Design-time and runtime validations for policy compliance with expanded examples.
Most enterprises operate with some level of internal and external regulation. Fugue validates policies expressed as code both with a compiler on an individual’s box and with a highly secure, no-touch runtime management and enforcement engine (Fugue’s Conductor) suited for teams and sensitive environments. The latter provides a fail-safe, preventing any noncompliant infrastructure from being provisioned. By these means, security and compliance “as code” can be reviewed and automated alongside infrastructure and feature code in a CI/CD system. Validations are easy to replicate, in a matter of seconds, across dev, test, staging, and production environments. Fugue offers new and expanded examples of useful validations around HIPAA and NIST SP 800-53 rules, as well as guidance from engineers and professionals to easily write your own.
Enhanced composition generation and visualization.
As the blueprints and source of truth for your cloud workloads, Fugue’s compositions provide concise infrastructure definitions—readable by humans for easy editing and by Fugue’s Composer for automated visualization and import. With the latest release, now you can automatically generate a composition from running infrastructure not under Fugue’s control, instantaneously see a visual map of it, learn whether and exactly how it violates policy validations, and bring it under Fugue’s control by importing it with a few clicks or a single command. Fugue’s interactive infrastructure visualizations continue to show your whole system and its integrated services in real time, with zoom and inspection features. This release improves visualization load times and spacing format for some services. For a full recap of the Composer’s functionality and advantages, check out our previous blog post and feature page.
Preview of Fugue’s REST API.
Fugue’s standards-based API ensures that enterprises can easily integrate Fugue operations into workflows and platforms, communicating over a single collection of HTTP endpoints rather launching multiple CLI instances. A full reference is available here. The API is compatible with REST clients (Postman, Insomnia, Paw, etc.) and HTTP clients (curl) to issue Fugue commands and manage cloud infrastructure. Exporting a single environment variable (export FUGUE_BETA_API=true) enables the fugue server command and use of the API. As the API is in preview, we welcome feedback.
Process-level RBAC.
Many enterprises need to enforce varying levels of access control for users and groups across multiple Fugue processes (i.e., individual composition instantiations managed by Fugue) within a single AWS account. You can now do that by applying role-based access control (RBAC) policy to specific Fugue processes. Once you’ve created a process (with a fugue run) and set a fairly restrictive account-level RBAC policy on Fugue’s Conductor, you can give varied permissions on those processes using the process-level RBAC. So, if Alice is an account admin and Bob is a developer, Alice is the only one who can launch processes; once she’s launched a process for Bob, she can give him permission to update that process, kill that process, etc. But Bob can’t touch Charlie’s processes in the same account. Team members working in same account gain secure, granular control over different processes.
Tunable Conductor enforcement.
Fugue’s Conductor is responsible for building, operating, enforcing, and tearing down infrastructure via Fugue processes. Enforcing infrastructure declarations in compositions is Fugue’s default state and a best practice—it means the Conductor automatically returns infrastructure straying for any reason to what’s specified in the composition. Fugue executes continuous runtime protection and repair via this mechanism. There are, however, use cases where a team lead may need to toggle enforcement from its ON state to OFF and back again. That’s achieved via the fugue property command’s enforcement key and --set flag. When configurable enforcement is OFF, Fugue is still managing your system, so runtime validations (which are attached to the Conductor) are active and honored. But, changes made to your infrastructure via the AWS Console or a different tool also can be honored while enforcement is OFF.
Process locking.
In addition to the enforcement key, the fugue property command now has a lock key. A team lead might lock three crucial Fugue processes out of several dozen so that, in a CI/CD scenario for example, a flawed shellscript managing Fugue commands can’t perform operations against those three processes. From a systems perspective, this is an extra safeguard that prevents inadvertent crashes of important infrastructure. A new field in Fugue’s status output called Flags shows lock state and enforcement state for each process.
Expanded region placement for the Conductor.
Along with Fugue’s ongoing coverage of the GovCloud region, you can now launch Fugue’s Conductor in most AWS regions across the globe. The same has long been true for your application’s infrastructure.
Improved high fidelity job status.
Roughly every 30 seconds Fugue sends a job through its system that inspects infrastructure or changes it (via creating, updating, or destroying). Improvements to the fugue history and fugue ops commands give a more granular view of those interactions. With fugue history, events, which are signals coming into the system such as an API call or command, are distinguished from jobs, in which the system is doing the actual work. The fugue ops command goes even further with improved granularity—listing all operations executed by Fugue against specific AWS services and resources associated with a particular job. And, you can even drill into that particular job via the job ID.
Migrating is Straightforward and Painless
The migration process is new with this product release and some AWS services are not yet covered, but the most commonly employed ones can be brought under Fugue’s governance in two steps, in a matter of minutes. Whether you’re using Fugue’s Composer or its CLI:
- First, Fugue scans existing AWS infrastructure in a region you specify and auto-generates infrastructure definitions in Fugue’s DSL, Ludwig, crafting an accurate composition that’s complete with simple function calls and human-friendly comments describing cloud services. The transcriber, downloaded with the client package, executes this scan and auto-generation, which you initiate in the Composer by filling in a few credentials fields and clicking a “Generate Composition” option or which you initiate on the CLI with the
fugue-transcribercommand. The Composer, as expected, also yields a complete, interactive visualization of transcribed infrastructure.
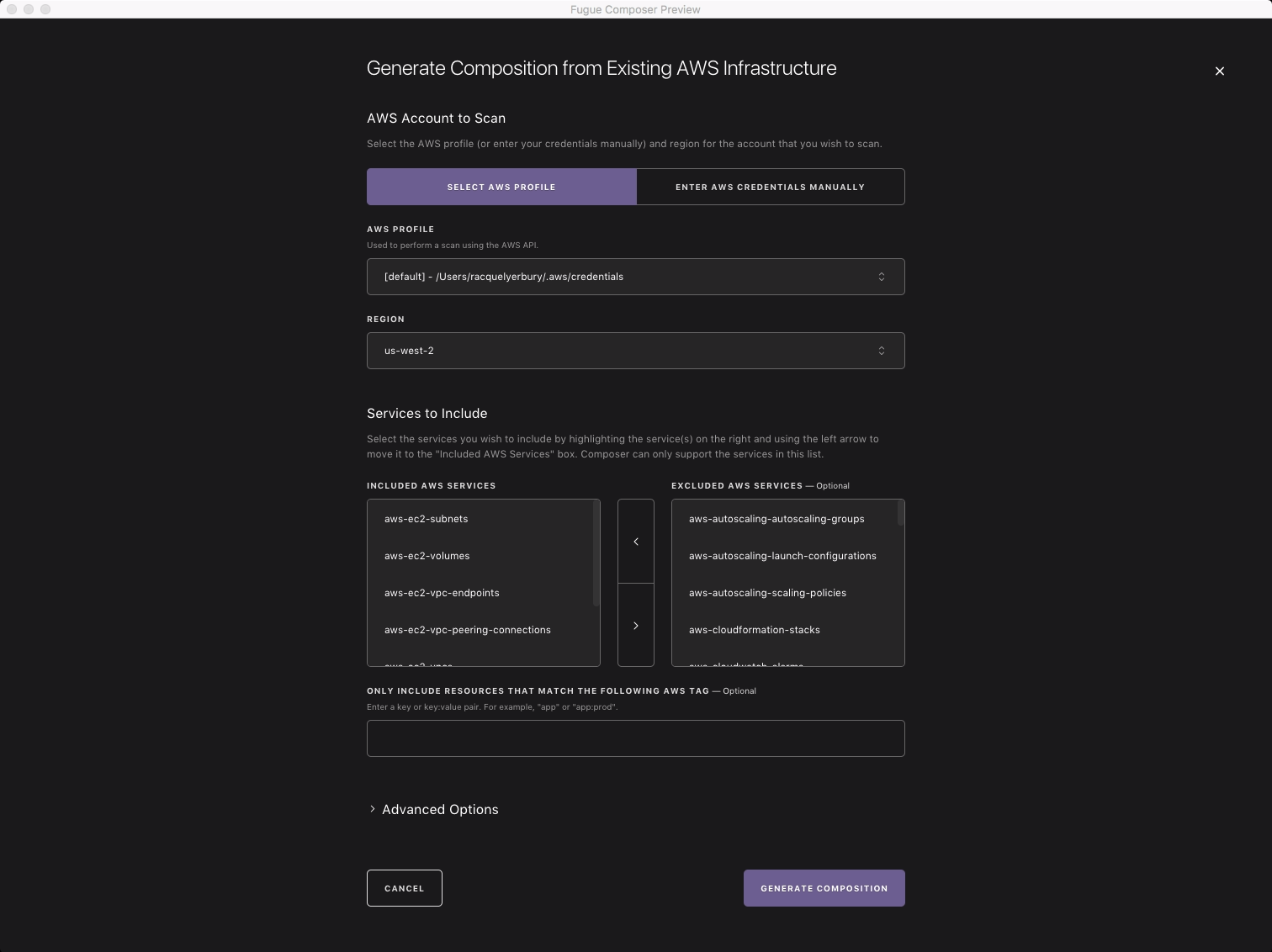
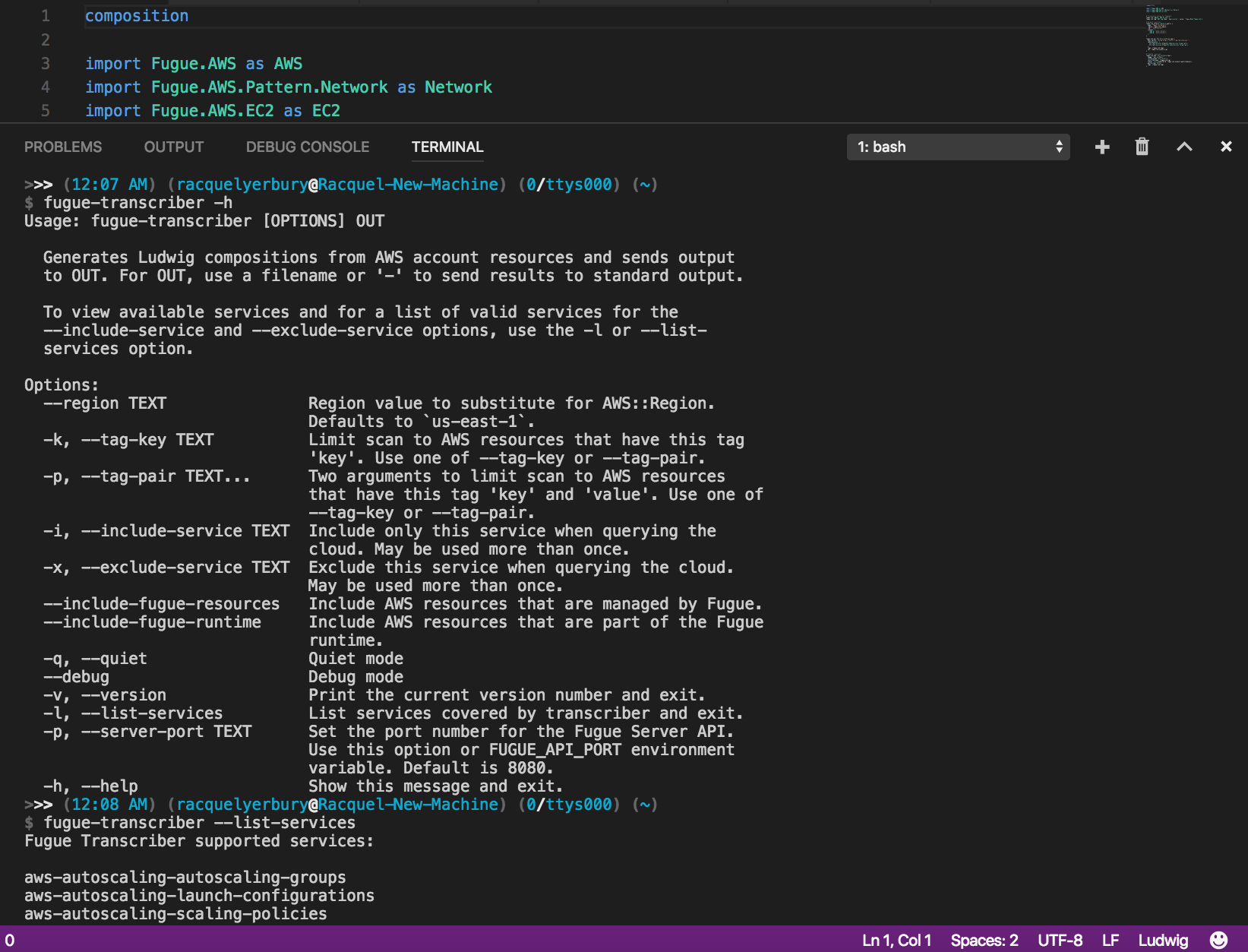
fugue-transcriber command and its options on the CLI to complete the first step.- Second, Fugue imports those existing resources you just transcribed, which previously were not controlled by Fugue. To do so, it creates a new process and populates that process with the selected infrastructure from your AWS account expressed in the transcribed composition. By initiating the import with either the Composer’s “Create New Process” option or the CLI’s
fugue runwith the new--importflag, you migrate your workloads to Fugue and enjoy the benefits of infrastructure governance.
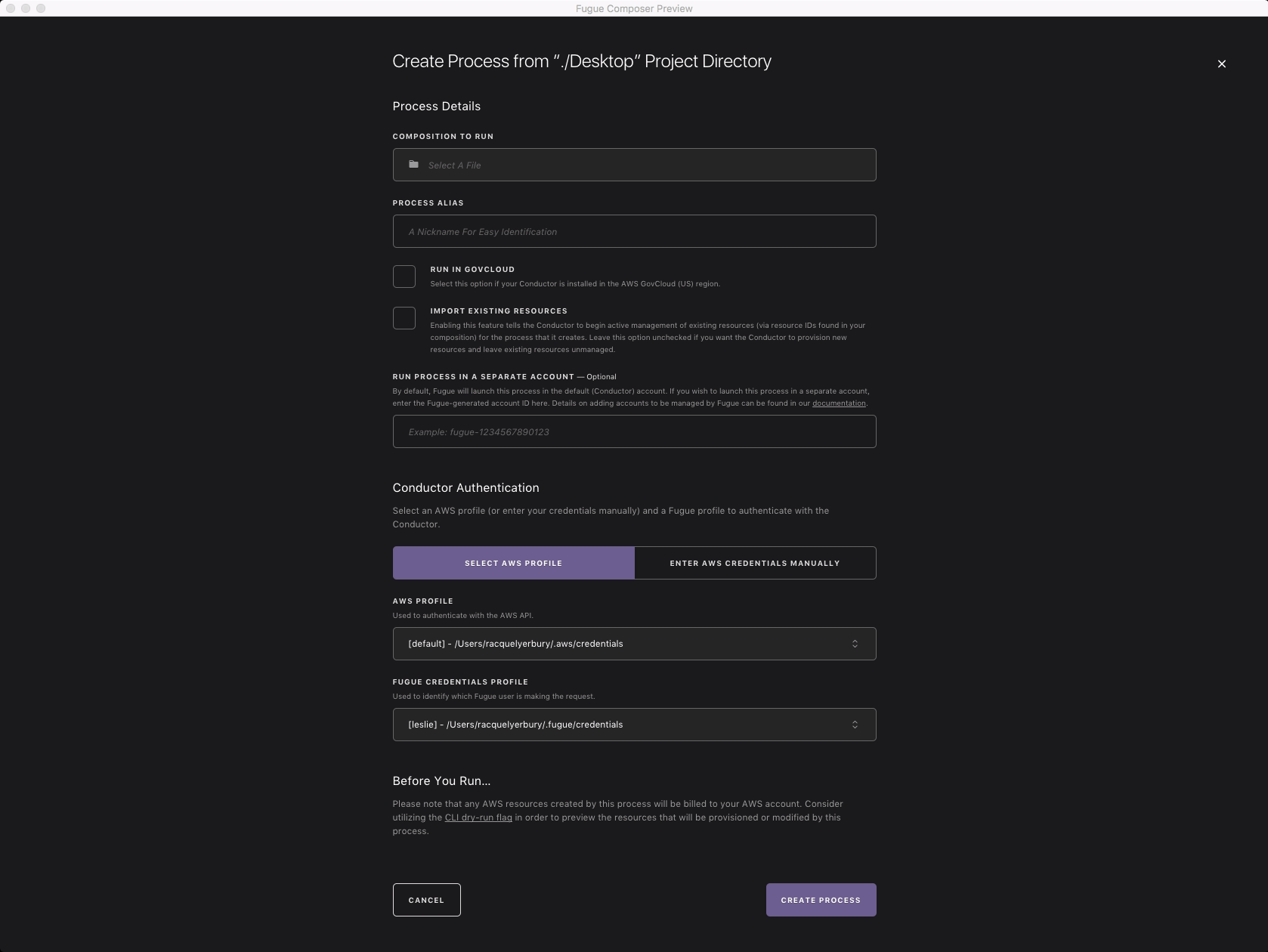
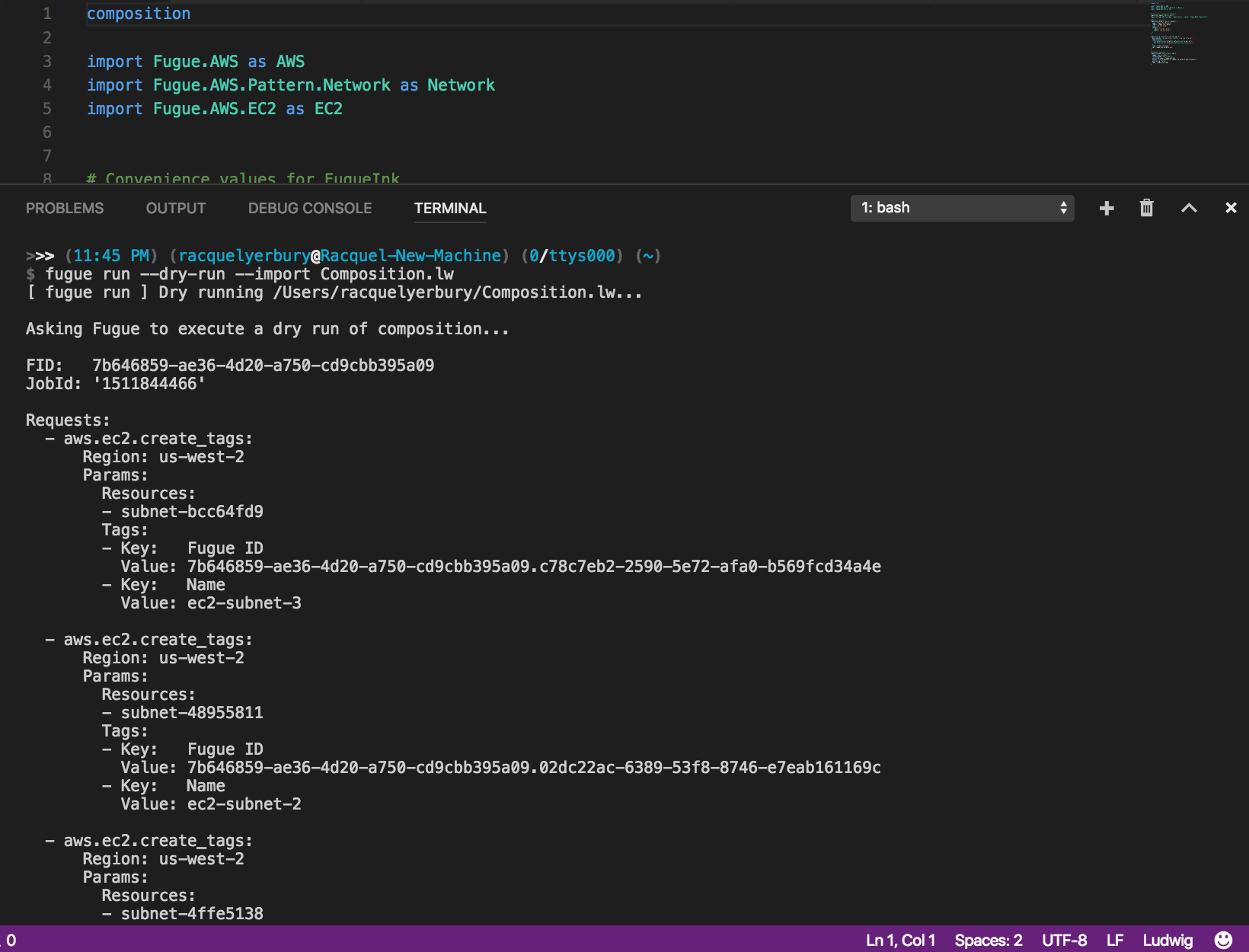
fugue run with the --import flag on the CLI, here shown with the --dry-run option also included, which provides the execution plan before Fugue takes ownership of the pre-existing infrastructure.Once you’ve completed these two steps (transcribing and importing), Fugue has taken control of what’s already running; it’s not going to create a second set of resources. With the import, you simply told Fugue to take ownership of the existing infrastructure that wasn’t previously controlled by Fugue. The transcribed composition, like any composition, is now your source of truth and its declarations will be continuously enforced. Check out the docs for more details.
Let Us Know What You Think
The growing number of new and exciting AWS services, in addition to the comprehensive menu already available in the Console, means a net positive of choice for cloud stakeholders. But, that brings with it an ever increasing complexity. Fugue is designed to give enterprises the robust cloud governance needed to move fast, see everything, and get cloud right. Now, with two-step migration of existing cloud resources to Fugue, it’s even easier to prevent costly mistakes and breaches before they happen.
We’re looking forward to your feedback on our latest release! Along with the new and enhanced features described in this post, the latest product release is chock full of stability and performance improvements. Stop by booth 1600 at AWS re:Invent or go to our homepage and give Fugue a spin!
