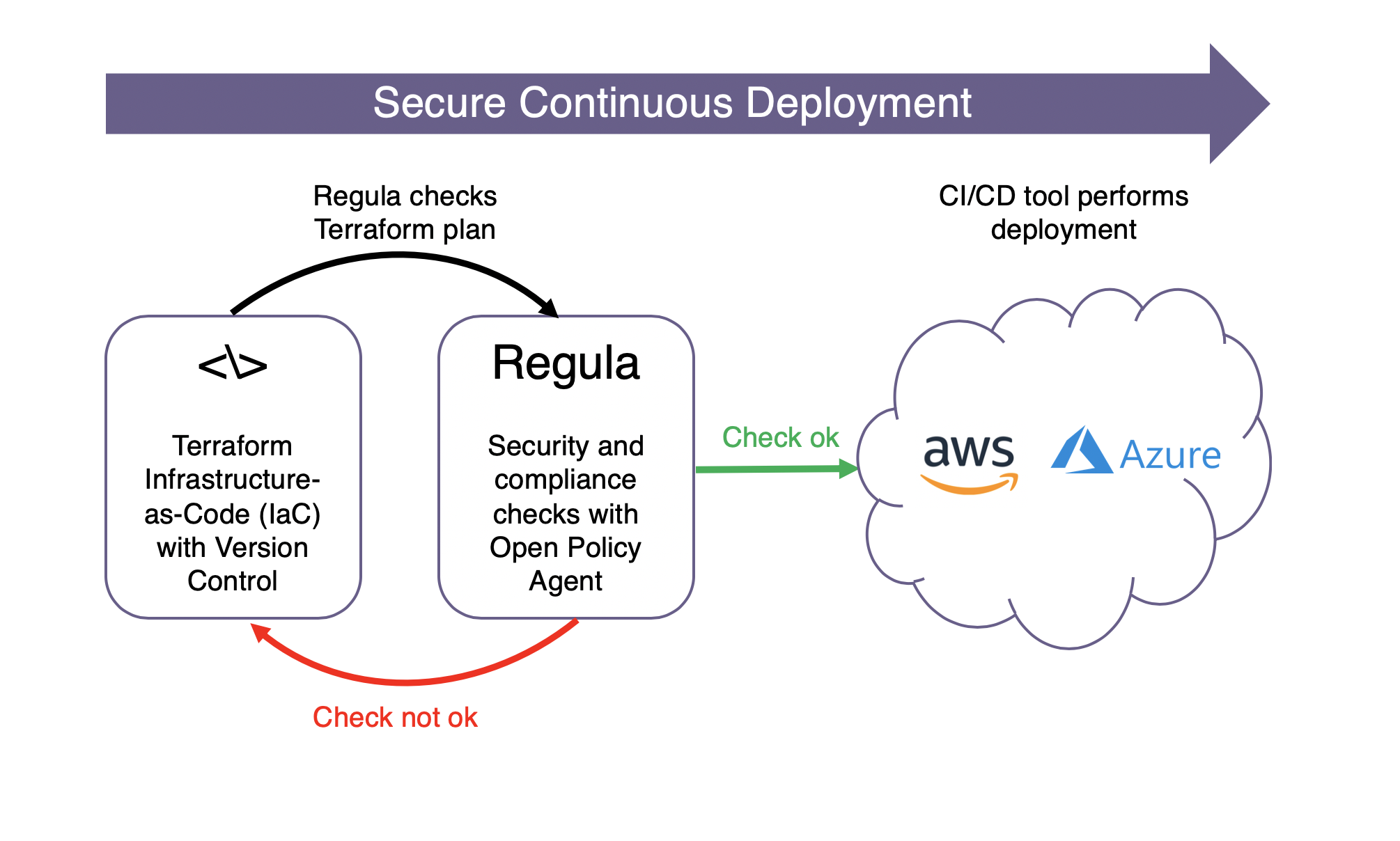
Today we announced Regula, an open source tool for evaluating Terraform infrastructure as code for potential security misconfigurations and compliance violations. Regula uses the open source Open Policy Agent(OPA) policy framework and Rego query language, which have gained significant traction in the Kubernetes community and scale to cloud infrastructure policy assessments as well (Fugue’s SaaS product performs more than 100 million policy evaluations using OPA every day).
While maintaining the security and compliance of cloud infrastructure requires the continuous evaluation of existing resources (what Fugue does), our customers often tell us that they want to validate their infrastructure-as-code for policy compliance to identify pre-deployment. We built and open sourced Regula to solve this problem.
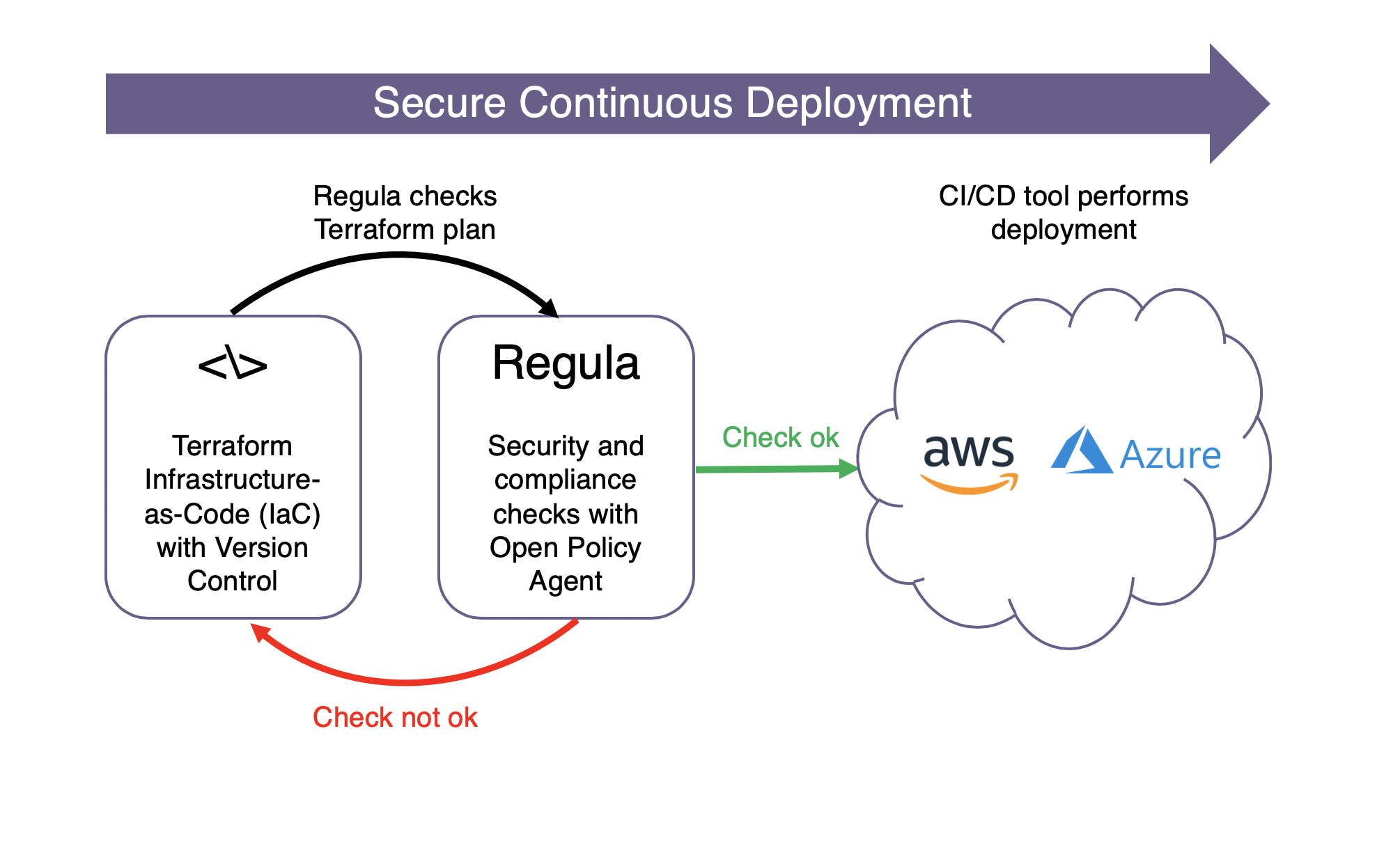
Regula identifies cloud misconfiguration risks contained in Terraform scripts. The initial release of Regula includes rules that can identify overly permissive IAM policies and security group rules, VPCs with flow logs disabled, EBS volumes with encryption disabled, and untagged cloud resources. View the full set of initial Regula rules here.
We are adding more rules over the next few weeks, and will be adding support for Azure as well.
Regula initially supports rules that validate Terraform scripts written for AWS infrastructure, and includes mapping to CIS AWS Foundations Benchmark controls where relevant. Regula also includes helper libraries that enable users to easily build their own rules that conform to enterprise policies. At launch, Fugue has provided examples of Regula working with GitHub Actions for CI/CD, and with Fregot, a tool that enables developers to easily evaluate Rego expressions, debug code, and test policies. Fugue open sourced Fregot this past November.
Working independently of Fugue, Regula can be integrated with Fugue for end-to-end cloud infrastructure security and compliance. Fugue enables users to visualize cloud infrastructure environments, detect post-deployment misconfigurations and automatically enforce critical resource configurations through self-healing. Both Regula and Fugue utilize the open-source Rego policy language, and developers can easily create their own rules for Regula and Fugue using a similar syntax. In addition to Fugue Enterprise, Fugue offers Developer, a free tier available to individual engineers who need to ensure continuous security and compliance of their cloud infrastructure environments.
Regula is available today on Fugue’s public GitHub repository.
One more thing…
Fugue is cloud security and compliance. Built for engineers, by engineers. With Fugue, you can:
- Get complete visibility into your cloud infrastructure environment and security posture with dynamic visualizations and compliance reporting.
- Validate compliance at every stage of your software development life cycle for CIS Foundations Benchmark, HIPAA, PCI, SOC 2, NIST 800-53, ISO 27001, GDPR, and your custom policies.
- Protect against cloud misconfiguration with baseline enforcement to make security critical cloud infrastructure self-healing.
Fugue Developer is free forever for individual engineers. Get started here.