Last week, Fugue released its Cloud Infrastructure Misconfiguration Report, which presents the results of our survey of more than 300 IT and security professionals from enterprise-level organizations. What surprised many of us at Fugue the most was the steep cost incurred by enterprises in their attempt to manage cloud misconfiguration, which is still largely a complex, manual process in an otherwise automated world of cloud. You can read more about that in The Cost of Cloud Misconfiguration Whack-a-Mole.
Today let’s focus on the risk that cloud misconfiguration brings to the enterprise, and what our survey reveals about the severity of the problem. In short, it’s bad. An overwhelming majority (93%) say they are “somewhat concerned” or “highly concerned” that their organization is at risk of a major security breach due to misconfiguration. Twenty-seven percent (27%) reported that their organization had already suffered a critical security breach due to misconfiguration, and 79% say critical misconfiguration events are still being missed.
"I’m seeing a lot of cloud configuration errors in the real world—and it’s scaring the hell out of me."
—David Linthicum, Chief Cloud Strategy Officer at Deloitte. "Cloud misconfiguration: The security threat too often overlooked." InfoWorld 05 October 2018.
What’s going on?
Why is cloud misconfiguration such a universal problem that puts enterprises at risk of critical breaches? In part it stems from the ease with which organizations can get up and running in the cloud and scale out their operations there. The largely manual, time-consuming change approval processes that dominated the datacenter simply don’t work well in fast-paced and dynamic cloud environments. There are simply too many resources, too much change, too many interfaces, and too many policies for humans to adequately track and govern.
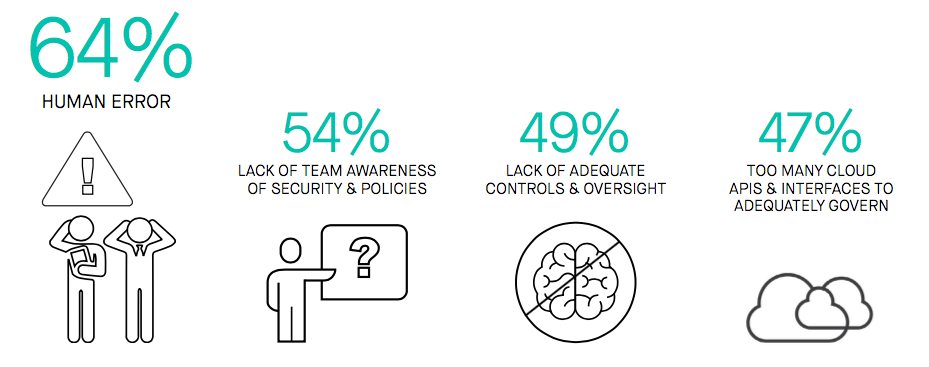
What’s at risk?
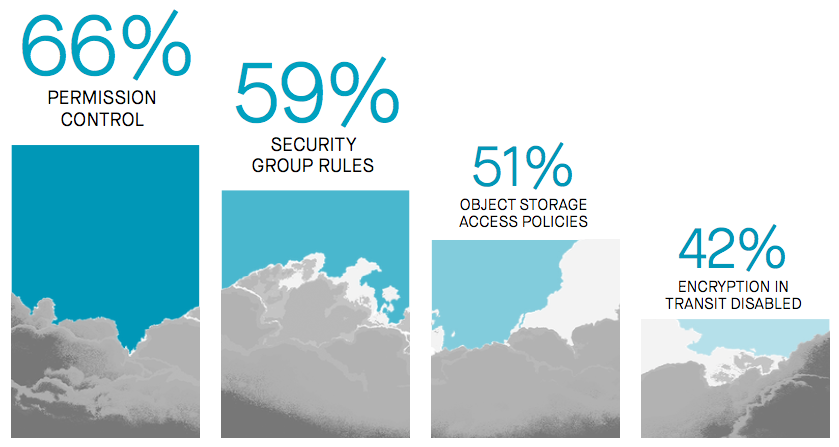
Respondents cited a vast number of different types of misconfiguration they commonly experience, and all can result in leaving the door open for bad actors to steal critical data. All it takes is for someone to open a port in order to retrieve server logs, or flip access on object storage (i.e., AWS S3; Azure Blob Storage) to public. Oftentimes, the least-privilege model for access control can become overly complex in the cloud, resulting in overly permissive roles. What this all means is that there are countless ways cloud infrastructure misconfiguration can expose critical data.
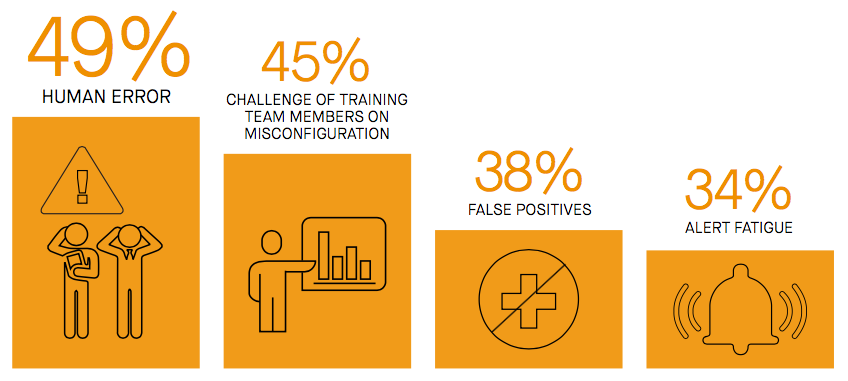
Manual solutions are too slow and prone to error
It’s not that infrastructure and security teams aren’t trying to do something to address the problem. They are. But an overreliance on monitoring and alerting tools and a lack of automation leaves enterprises will little assurance that infrastructure is secure and configuration adheres to compliance policy. When daily misconfiguration events per team typically number in the dozens, or hundreds, this becomes a costly game of whack-a-mole that every enterprise is playing. And they’re losing.
For the vast majority, the task of identifying critical misconfiguration events, adding them to the queue, and remediating them, is entirely manual and time-consuming. When it comes to misconfiguration risk, time is your enemy, and any delay in remediating them increases risk.
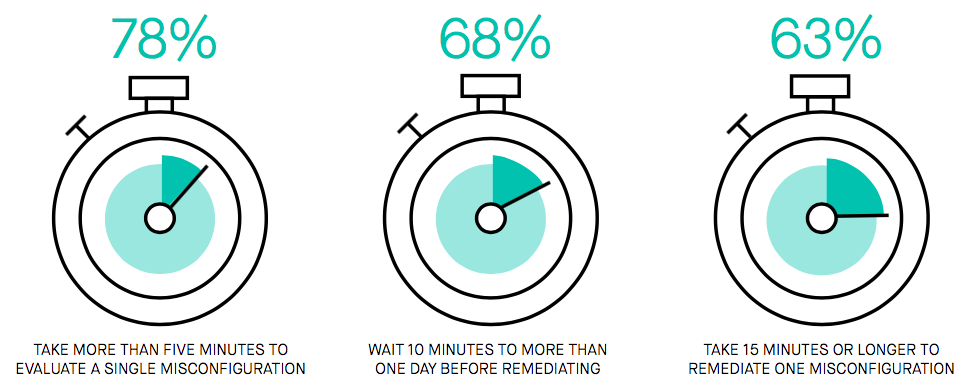
Long MTTRs bring significant risk
Many threats to cloud infrastructure are automated, constantly probing networks and endpoints looking for misconfiguration to exploit. As we can see from the survey results, the manual approaches to managing misconfiguration take too long to provide adequate assurance that this risk is mitigated against automated threats.
While a majority of respondents feel an ideal Mean Time to Remediation (MTTR) for misconfiguration would be under one hour, the sad fact is that MTTRs of one day are the norm.
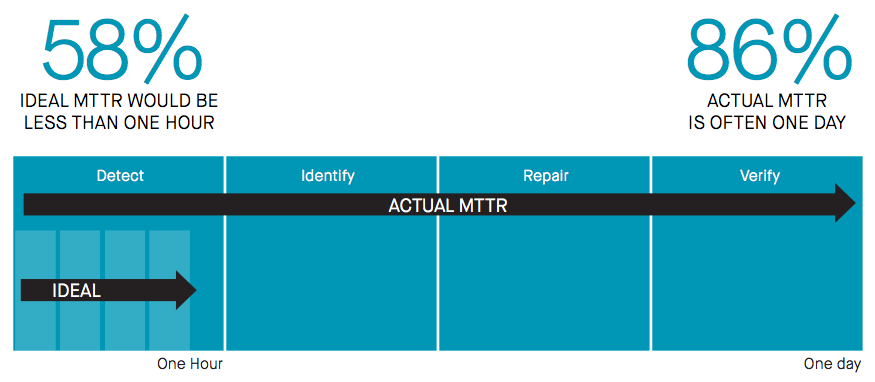
In the cloud, automation reigns. Whether it's CI/CD, provisioning, or monitoring, if there's a common, repetitive task, you can bet it's been automated. With one big exception: cloud infrastructure security.
Is automated remediation the answer?
Survey respondents overwhelmingly see value in automated remediation as a better solution to managing cloud misconfiguration risk and increasing efficiency.
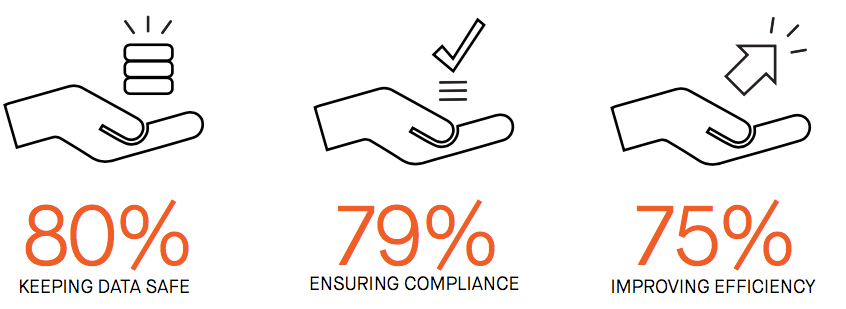
The concept of automated remediation does not come without legitimate industry baggage, including concerns about false positives leading to bad changes, maintainability and scalability, and issues about who “owns” remediation. To address these concerns, it’s important that enterprises consider automated remediation solutions that are tightly integrated with DevOps by reverting unauthorized changes back to the known-good baseline they originally provisioned. And it’s critical to avoid approaches that require maintaining separate automation scripts, rely on blacklists, or only cover a small subset of cloud resources.
Download our free Cloud Infrastructure Misconfiguration Report.
