Enforce enterprise IAM security requirements
Leverage the Unified Policy Engine to apply enterprise-specific rules
- Write custom rules for your organization's IAM requirements using the simple and powerful Rego language
- Monitor for common IAM issues such as overly permissive policies, publicly accessible resources, and unrotated credentials
- Detect complex IAM vulnerabilities involving multiple resources, such as AWS IAM roles attached to instance profiles that allow list actions on S3 buckets
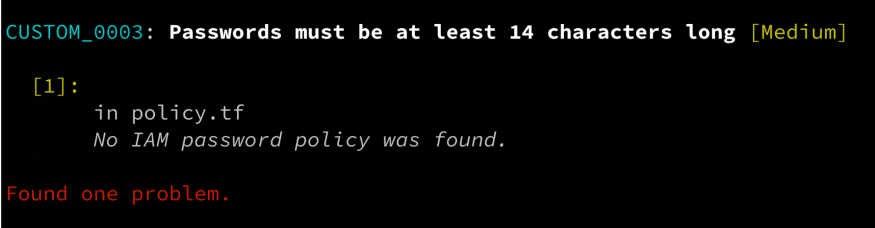
Protect IAM across the entire SDLC
Audit and secure your IAM posture pre- and post-deployment
- Check IAM permissions in infrastructure as code during the development process, and fix issues before they reach the runtime
- Build IAM checks into CI/CD pipelines using Regula, an open-source tool powered by OPA
- Quickly identify and remediate policy violations and configuration drift at runtime
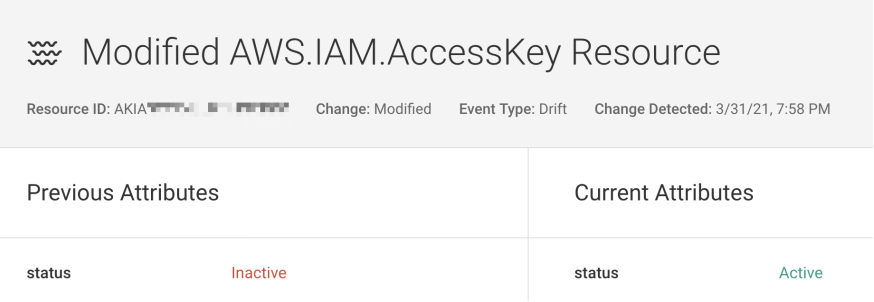
Gain complete visibility into IAM
Simplify IAM complexity with Fugue's standardized views
- Review unified compliance and security reports across AWS, Azure, and Google
- Inspect IAM principals and service accounts in an interactive diagram and see associated policies
- Get notified about every configuration change to IAM policies and permissions

