What is the CIS AWS Foundations Benchmark?
The CIS AWS Foundations Benchmark is a compliance standard for securing Amazon Web Services resources. The benchmark offers prescriptive instructions for configuring AWS services in accordance with industry best practices. In May 2018, the Center for Internet Security (CIS) published version 1.2.0. CIS AWS recommendations are decided upon by consensus of independent security experts.
Why is CIS AWS Compliance Important?
Any organization that uses cloud resources provided by Amazon Web Services can help safeguard sensitive IT systems and data by complying with the CIS AWS Foundations Benchmark. Cloud misconfigurations and cyber attacks are a constant concern for organizations that operate in the cloud, so security is of utmost importance.
CIS notes that the benchmark is for anyone who plans to "develop, deploy, assess, or secure solutions in Amazon Web Services," so DevOps personnel, security analysts, and compliance analysts in particular can benefit from evaluating their infrastructure against the benchmark and adhering to its recommendations.
CIS AWS Foundations Benchmark Compliance
The CIS AWS Foundations Benchmark is composed of 4 sections with a total of 49 controls known as "recommendations."
The 4 sections include:
1. Identity and Access Management
The first section contains recommendations for configuring IAM-related options. For example, CIS AWS 1.11 encourages users to "Ensure IAM password policy expires passwords within 90 days or less." Regular password changes can limit the risk of a breach due to stolen or compromised passwords, reuse of the same password in different systems, and other potentially dangerous situations. Organizations can promote password hygiene by creating a password policy that requires users to create a new password every 90 days or less.
2. Logging
The second section contains recommendations for configuring account logging features. CIS AWS 2.7 suggests that users "Ensure CloudTrail logs are encrypted at rest using KMS CMKs." Using KMS customer master keys to encrypt CloudTrail log files provides additional confidentiality controls on log data. For each CloudTrail trail, enable encryption and specify a KMS key ID.
3. Monitoring
The third section contains recommendations for configuring AWS log metric filters and alarms to monitor services. To comply with CIS AWS 3.1, "Ensure a log metric filter and alarm exist for unauthorized API calls," you can direct CloudTrail logs to CloudWatch logs and establish a corresponding metric filter and alarm. Monitoring API calls can help decrease the time needed to detect malicious activity, so set up a metric filter, alarm, SNS topic, and subscription to track suspicious calls.
4. Networking
The fourth section contains recommendations for configuring security-related VPC attributes. For example, CIS AWS 4.1, "Ensure no security groups allow ingress from 0.0.0.0/0 to port 22," helps prevent the internet at large from accessing your servers through SSH. You can achieve this by auditing your security groups and removing any inbound rules that allow unrestricted traffic to port 22.

Detect Compliance Violations
Fugue continuously evaluates your cloud environments for CIS AWS compliance violations with predefined rules mapped to CIS AWS compliance controls. If a resource is determined as non-compliant, an alert will be sent to notify the compliance team. The compliance team can then determine whether to correct the non-compliant resource and set an established baseline for future enforcement.
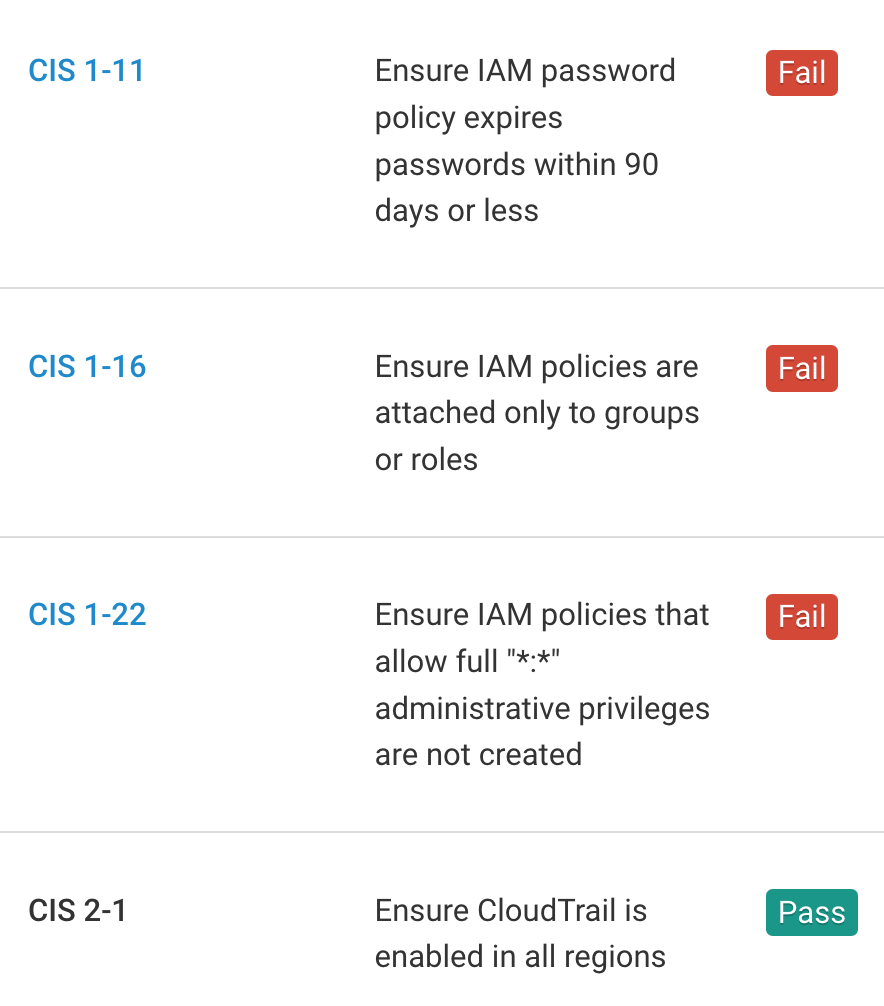
Detect Compliance Violations
Enforce Baselines with Codeless Auto-Remediation
Fugue utilizes baselines to auto-remediate and correct compliance violations via self-healing. With baseline enforcement, misconfiguration is automatically corrected back to the CIS AWS compliant baseline without writing automation scripts.
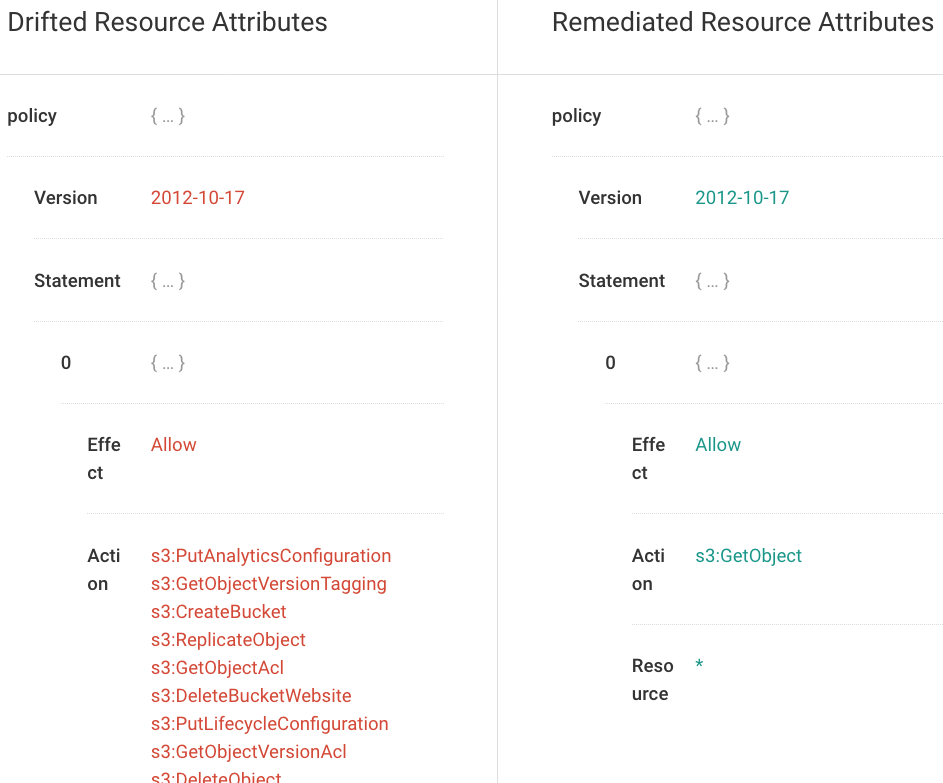
Enforce Baselines with Codeless Auto-Remediation
Report on Compliance Posture
Fugue makes it easy to report on your CIS AWS compliance posture. Detailed reports, dashboards, and visualizations are available to easily track and monitor your cloud resources. Daily or weekly reports highlighting compliant and non-compliant resources can be emailed to executives or auditors to show proof of compliance.
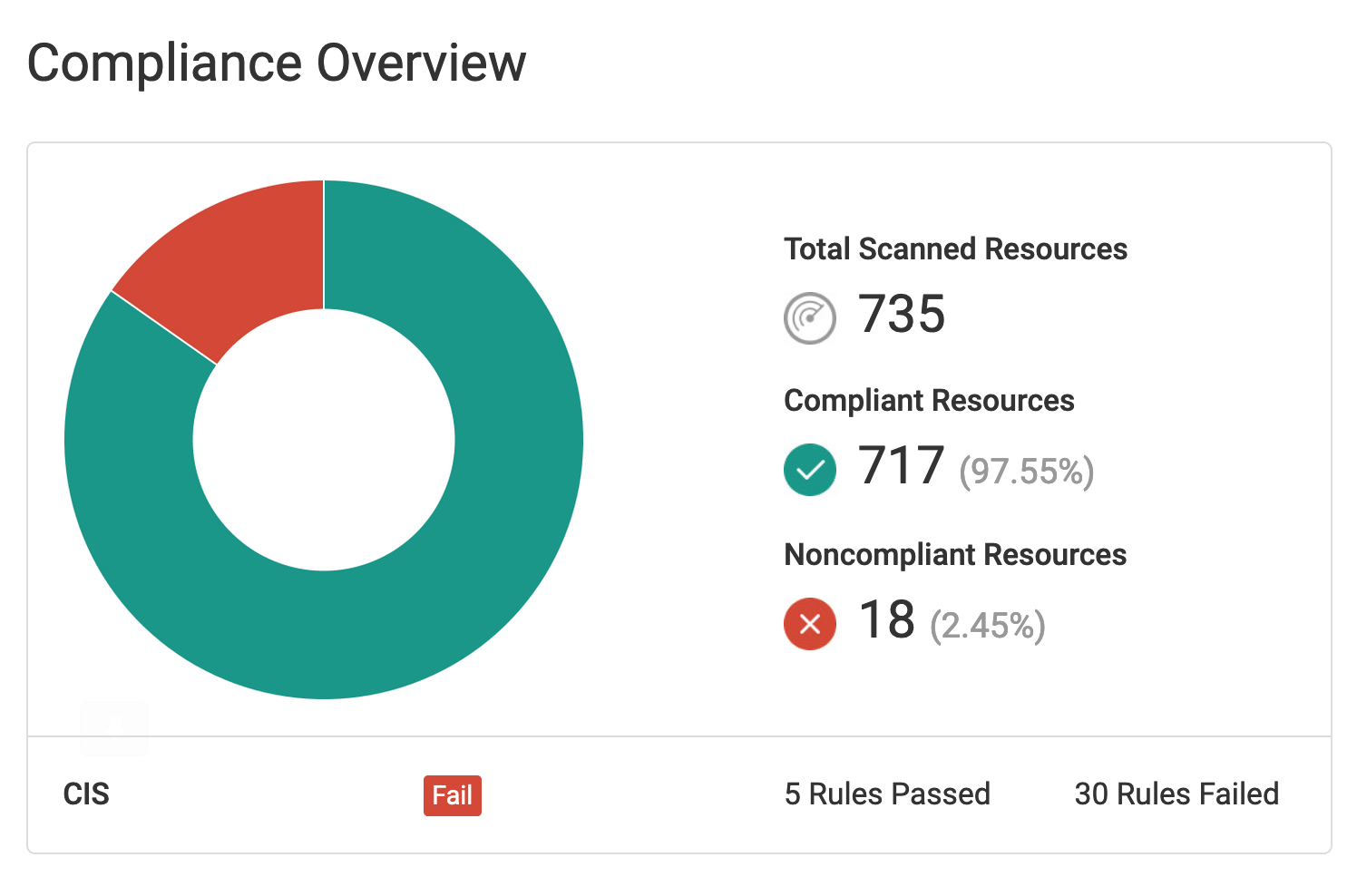
Compliance Overview
