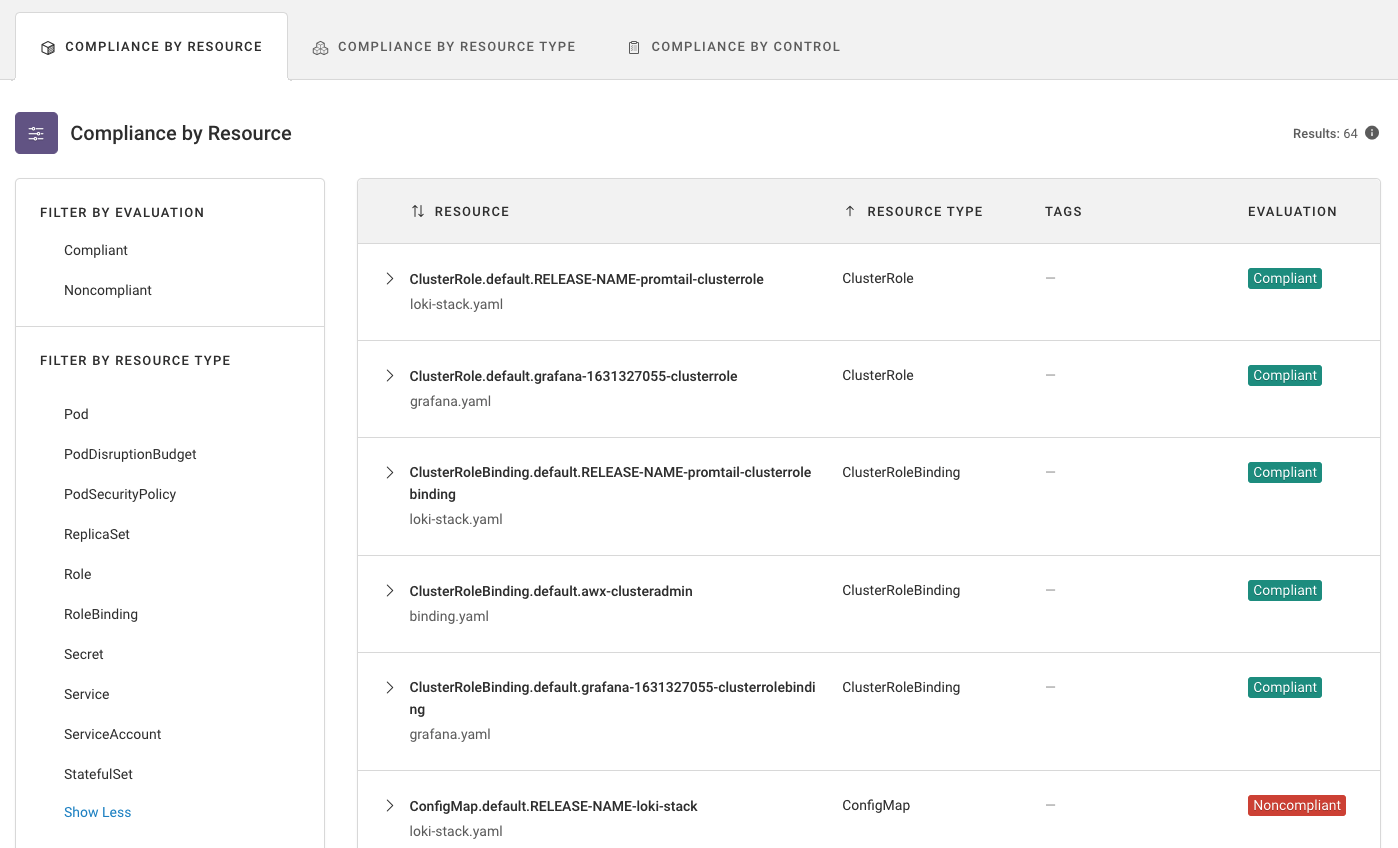
Pre-deployment checks on cluster configurations
Validate cluster configurations before any infrastructure is deployed
- Catch issues in configuration code before clusters are deployed with Amazon ECS/EKS, Azure AKS, Google GKE, or native Kubernetes
- Leverage Fugue’s prebuilt library of checks mapped to the CIS Docker and CIS Kubernetes Benchmarks
- Develop custom rules—including multi-resource checks—using Rego, the simple and powerful open source language from Open Policy Agent
Runtime infrastructure security
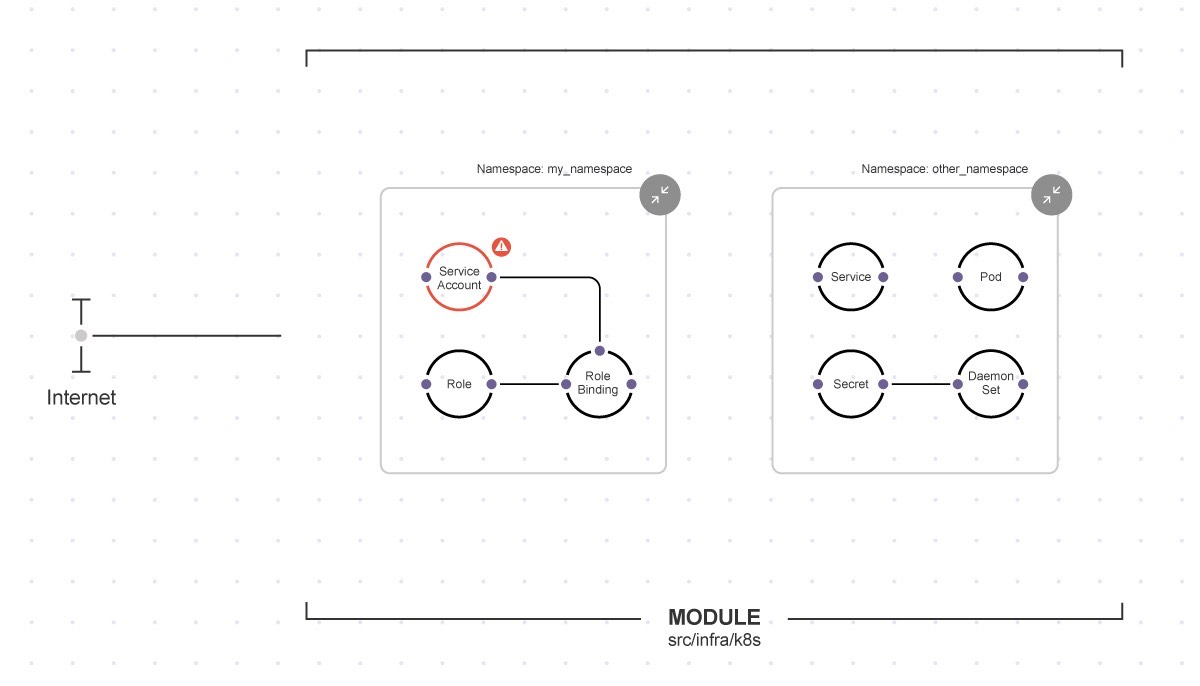
Secure the underlying cloud infrastructure for containers and clusters
- Visualize and inspect your clusters within a broader infrastructure context—including underlying VMs, IAM permissions, and storage services such as Amazon S3
- Identify unused resources, including orphaned infrastructure
Tools for security engineers
Ensure that container and Kubernetes security integrates with your engineering tools and workflows
- Integrate pre-deployment checks into git workflows and CI/CD pipelines with Regula—Fugue’s open source IaC security project
- Automate security scans with Fugue’s API and CLI tools
- Send reports and notifications to your team to keep them in the loop
