Misconfiguration and Data Breaches
According to Gartner, by 2020, 95% of cloud security issues will be the result of misconfiguration or mistakes. A single misconfiguration can expose hundreds or thousands of systems or highly sensitive data to the public internet.
What may be described as a "data breach" is more often a cloud storage bucket containing sensitive data that is accidentally exposed to the internet. Many high profile breaches have raised interest in CSPM.
Here are a few examples of data breaches due to cloud misconfigurations.
540M
Facebook member records exposed by an unsecured AWS S3 bucket
1.8M
Voter records exposed in an AWS S3 configuration blunder in Chicago
AWS S3
Server leaks data from Fortune 100 companies: Ford, Netflix, and Capital One
Why Do Misconfigurations Occur?
Misconfigurations are made possible by at least four factors:
- The cloud is inherently programmable.
Cloud infrastructure is driven by cloud applications and APIs, which enable developers to scale up and spin down large amounts of infrastructure via code. As easy as it is to make infrastructure changes, it is also just as easy to introduce misconfigurations. - The cloud has enabled a “sprawl” of new services and technologies.
When concepts such as microservices are combined with new technologies such as containers, Kubernetes, and serverless Lambda functions, there are many more resources to manage than just traditional servers, networks, and databases. - The cloud features fundamentally new technologies that are quite different than what are found in physical data center environments.
For example, IAM permissions enable users to access resources in an account regardless of network segmentation. IAM therefore can facilitate a new type of lateral movement that cannot be detected with traditional security tools. As organizations look to increase their cloud footprint, they are realizing that their IT staff may be lacking cloud security expertise. - The size and complexity of enterprise environments make it incredibly difficult to know what is running where.
Typical public cloud infrastructure can contain thousands or tens of thousands of resources, regions, and accounts. It can be very easy for a developer to create the wrong resource, be too liberal with permissions, or lose track of where critical cloud assets are stored.
All of these factors are compounded by the lack of visibility into the cloud. Many enterprises have no idea what type and how many cloud resources are running and how they are configured. As a result, serious misconfigurations often go undetected for days, weeks, or even longer, and taking the appropriate measures to secure cloud services and applications can be a challenge. A majority of successful attacks on cloud services are due to misconfigurations, and CSPM can help to mitigate these risks.
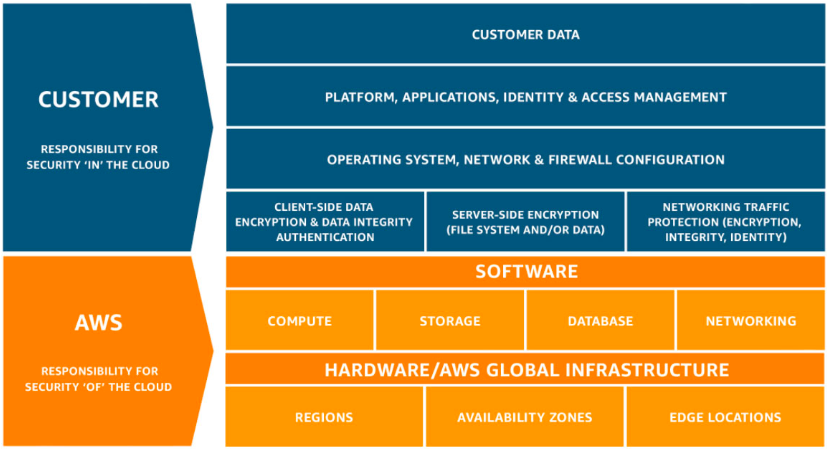
The Shared Responsibility Model
Security is a shared responsibility between the cloud provider—such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform—and the customer. In this "shared responsibility model," the cloud vendor is responsible for “security of the cloud,” which includes all the infrastructure that runs cloud services. While the major cloud providers go to great lengths to secure the infrastructure of their environment, it is up to the customer to secure their use of the cloud services. The customer is responsible for “security in the cloud."
Despite this model, there remains confusion about the demarcation of responsibility between cloud providers and their customers. According to a Barracuda Networks survey of 550 IT decision makers, 64% of respondents claimed that their cloud provider should protect customer data in the cloud, which is clearly the customer’s responsibility according to the Shared Responsibility Model.
With modern businesses moving their data into the cloud, this dangerous disconnect between perception and reality can leave many businesses vulnerable. This is why, according to Gartner, through 2023 at least 99% of cloud security failures are the result of human mistakes.
Why is CSPM Important?
Cloud Security Posture Management (CSPM) is defined by Gartner as "a continuous process of cloud security improvement and adaptation to reduce the likelihood of a successful attack." The unique nature of the cloud requires a new security concept that can address the distributed and constantly changing cloud infrastructure. CSPM security tools are continuously monitoring enterprise cloud environments to identify gaps between their stated security policy and the actual security posture and mitigate any cloud security risks that might occur.
At the heart of CSPM is the detection of cloud misconfiguration vulnerabilities that can lead to compliance violations and data breaches. CSPM offerings typically use APIs of the underlying cloud providers to monitor environments for security or policy violations with the option of remediating the violations to ensure compliance with policies.
Some of the benefits of CSPM include:
- Continuous visibility of multi-cloud environments to identify cloud misconfiguration vulnerabilities
- Optional ability to perform automated remediation of misconfigurations to ensure continuous compliance and protect critical cloud services
- Leverage of prebuilt compliance libraries of common standards or best practices such as CIS Foundations Benchmarks, SOC 2, PCI, NIST 800-53, or HIPAA to verify that configurations are compliant
CSPM Uses
CSPM offerings typically focus on identifying the following types of policy and security violations:
- Lack of encryption on databases or data storage.
- Lack of encryption on application traffic, especially that which involves sensitive data.
- Improper encryption key management such as not rotating keys regularly.
- Overly liberal account permissions.
- No multi-factor authentication enabled on critical system accounts.
- Misconfigured network connectivity, particularly overly permissive access rules or resources directly accessible from the internet.
- Data storage exposed directly to the internet.
- Logging is not turned on to monitor critical activities such as network flows, database access, or privileged user activity.
Fugue and CSPM
Fugue is an enterprise CSPM solution developed for engineers, by engineers. Fugue is different in that it addresses cloud security as a software engineering problem—because the cloud is 100% software. Fugue builds a complete model of your public cloud infrastructure environment as a baseline, continuously detecting drift and enforcing the baseline for security-critical resources. With Fugue, you get full visibility into your cloud security posture and the assurance that it stays in continuous compliance.
In modern cloud operations, security must be integral to the software development process, rather than bolted on after the fact as a security analysis function. With Fugue’s API, cloud security and compliance can be integrated into CI/CD pipelines for provisioning guardrails and to empower developers to validate compliance and check for security violations earlier in the software development life cycle. Fugue supports custom policies as well as frameworks for CIS Foundations Benchmarks, CIS Controls, CIS Docker, CSA CCM, GDPR, HIPAA, ISO 27001, NIST 800-53, PCI, SOC 2, and Fugue Best Practices. Fugue is available for AWS, Azure, and Google Cloud.