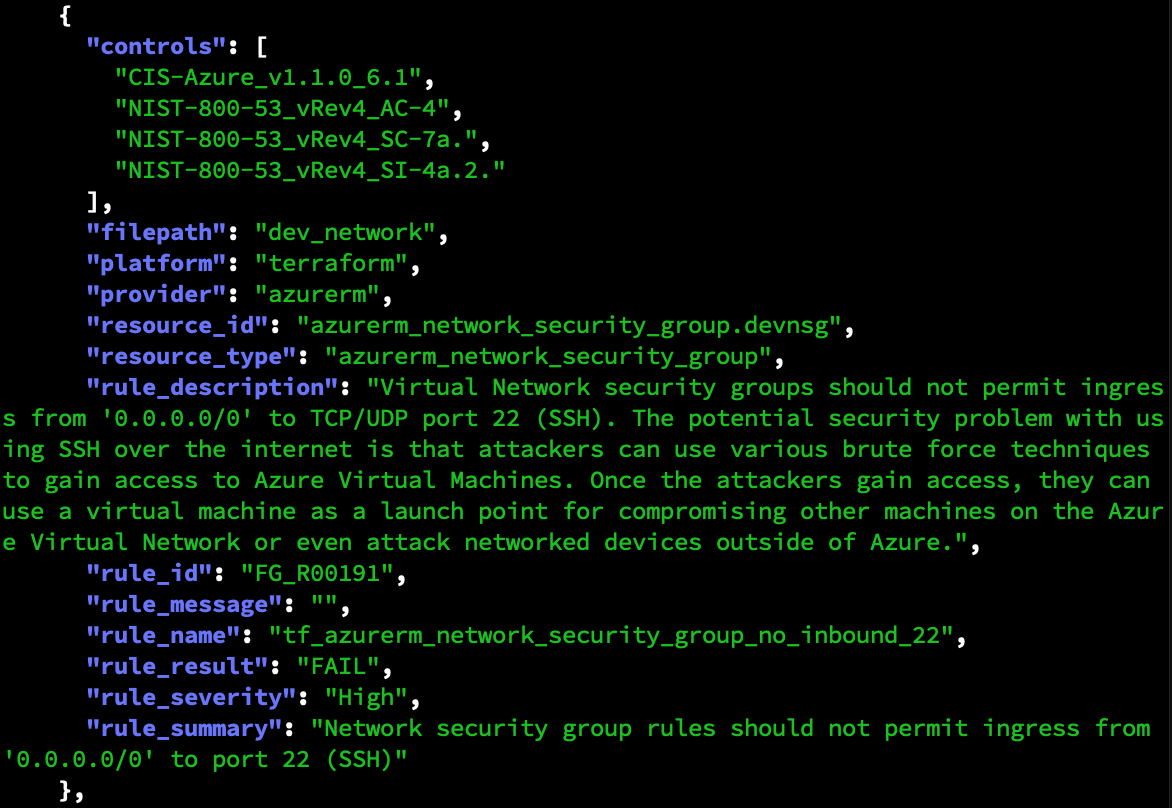
Detect Common and Complex Vulnerabilities
Identify resource misconfigurations that lead to system compromise
- Find common vulnerabilities such as overly broad access policies or user permissions
- Leverage powerful Regula Policy Engine to detect complex vulnerabilities encompassing multiple resource types
Track Cloud Indicators of Compromise (IoCs)
Use IoCs to reconstruct how cloud resources are misconfigured and exploited
- Identify which resource misconfigurations are cloud Indicators of Compromise that enable breaches
- Investigate IoCs by inspecting and verifying drift events (i.e. unvalidated configuration changes)
- Create a forensic audit trail of resource changes to reconstruct how breaches occur
Automated Remediation of Vulnerable Misconfigurations
Prevent breaches by automatically remediating vulnerable misconfigurations
- Create complete forensic audit trail of all resource configuration changes
- Leverage audit trail to automatically undo misconfigurations that lead to compromise
- Review an event stream of remediations to provide full visibility into automated actions

