What is the CIS Azure Foundations Benchmark?
The CIS Azure Foundations Benchmark is a compliance standard for securing Microsoft Azure resources. The benchmark offers prescriptive instructions for configuring Azure services in accordance with industry best practices. In February 2019, the Center for Internet Security (CIS) published version 1.1.0. CIS Azure recommendations are decided upon by consensus of independent security experts.
Why is CIS Azure Compliance Important?
Any organization that uses cloud resources provided by Azure can help safeguard sensitive IT systems and data by complying with the CIS Azure Foundations Benchmark. Cloud misconfigurations and cyber attacks are a constant concern for organizations that operate in the cloud, so security is of utmost importance.
CIS notes that the benchmark is for anyone who plans to "develop, deploy, assess, or secure solutions that incorporate Microsoft Azure," so DevOps personnel, security analysts, and compliance analysts in particular can benefit from evaluating their infrastructure against the benchmark and adhering to its recommendations.
CIS Azure Foundations Benchmark Compliance
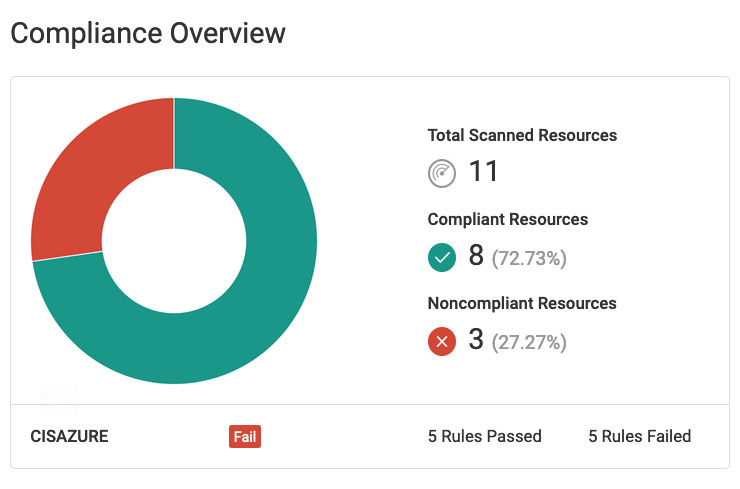
The CIS Azure Foundations Benchmark is composed of 9 sections with a total of 111 controls known as "recommendations." Below are examples from 3 sections, including recommendations and compliance information for each.
3. Storage Accounts
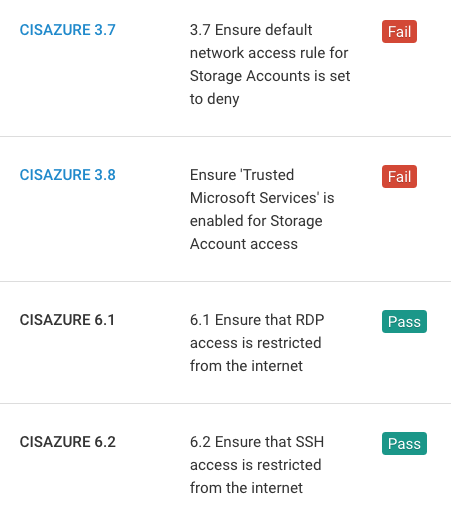
Section 3 contains recommendations for configuring storage accounts. For example, CIS Azure 3.1 encourages users to "Ensure that 'Secure transfer required' is set to 'Enabled.'" By requiring all requests to the storage account to use a secure connection, this recommendation ensures that insecure requests -- such as those made over HTTP -- will fail. Requiring secure transfer for storage accounts is disabled by default, so to comply with 3.1, simply enable the "Secure transfer required" setting.
6. Networking
Section 6 contains recommendations for configuring security-related VNet attributes. CIS Azure 6.2, "Ensure that SSH access is restricted from the internet," helps prevent the internet at large from accessing your Azure virtual machines through SSH. You can meet this recommendation by auditing your network security groups and removing any inbound security rules that allow unrestricted traffic to port 22.
7. Virtual Machines
Section 7 contains recommendations for configuring virtual machines. CIS Azure 7.2 suggests that users "Ensure that 'Data disks' are encrypted." By encrypting non-boot data disk volumes, organizations can adhere to the security best practice of enabling encryption at rest. Unencrypted data disks pose a security threat as a bad actor can steal or gain unauthorized access to data. To prevent such a threat, enable encryption for data disks attached to your virtual machines.
Detect Compliance Violations
Fugue continuously evaluates your cloud environments for CIS Azure compliance violations with predefined rules mapped to CIS Azure compliance controls. If a resource is determined as noncompliant, an alert will be sent to notify the compliance team. The compliance team can then determine whether to correct the noncompliant resource and set an established baseline for future enforcement.
Eliminate Azure Misconfiguration
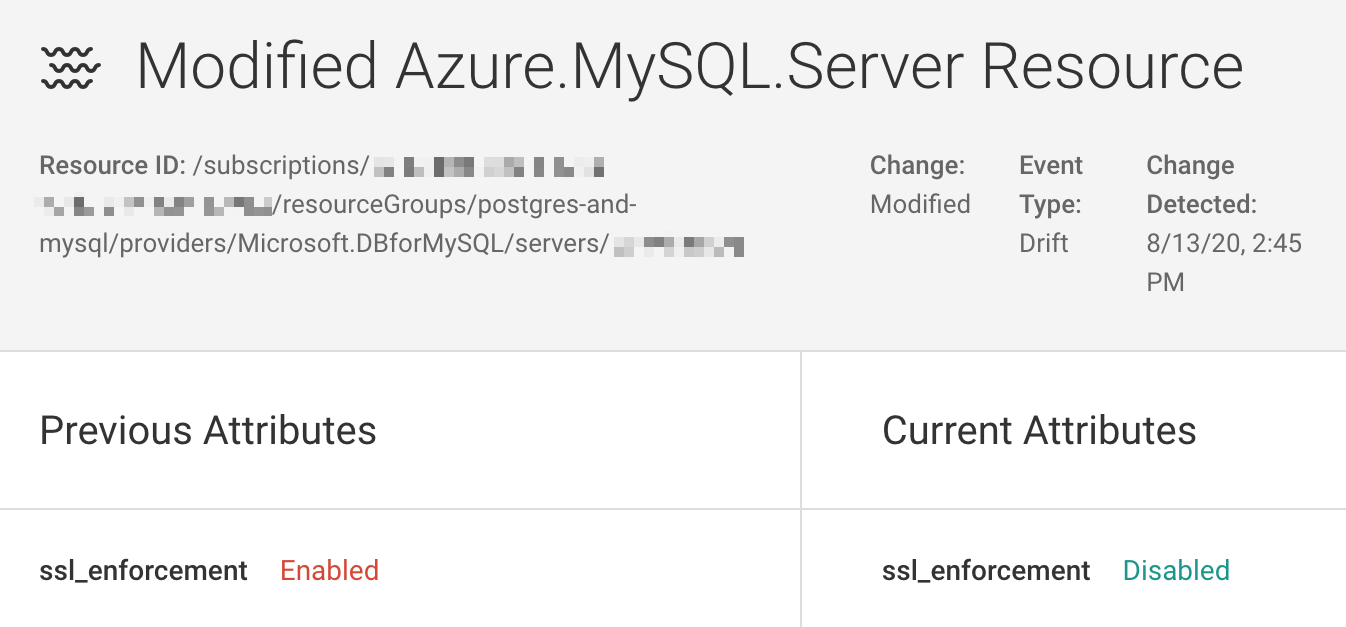
Fugue enables you to investigate potentially dangerous misconfigurations in near real-time. For instance, if an Azure Virtual Network is altered to allow unwanted SSH access from the internet, Fugue shows this and allows you to quickly remediate.
Report on Compliance Posture
Fugue makes it easy to report on your CIS Azure compliance posture. Detailed reports, dashboards, and visualizations are available to easily track and monitor your cloud resources. Daily or weekly reports highlighting compliant and noncompliant resources can be emailed to executives or auditors to show proof of compliance.