As more enterprises adopt the cloud, the issue of cloud security has become a top priority. The cloud is fundamentally different than the datacenter. Just as it requires a shift in how we think about architecture and operations, we need to shift our thinking on cloud security and compliance and bake it into DevOps and CI/CD processes (i.e., DevSecOps) rather than bolt it on later. Failing to do so puts your organization at serious risk of a critical data breach.
Infrastructure misconfiguration is the number one cloud risk
Fugue recently released its Cloud Infrastructure Misconfiguration Report, which found that 93 percent of IT and security professionals are concerned that their organization is at risk of a major security breach due to misconfiguration, and twenty-seven percent (27%) say they’ve already suffered such a breach. David Linthicum, Chief Cloud Strategy Officer at Deloitte, writes in InfoWorld that he’s “seeing a lot of cloud configuration errors in the real world—and it’s scaring the hell out of me.”
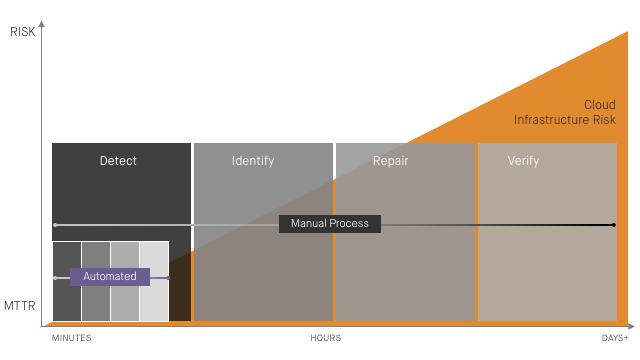
That doesn’t mean enterprises aren’t trying to address the problem, it’s just that they’re falling short of effectively mitigating the risk. While most are using some kind of cloud monitoring tool, there’s an over-reliance on manual processes for identifying and remediating critical misconfiguration events. It’s a costly, time-consuming burden that runs the risk of human error and long MTTRs (Mean Time to Remediation)—the time in which misconfiguration leaves enterprises vulnerable to exploitation.
Traditional methods of automated remediation are highly problematic
In the cloud, any repetitive manual task is going to get automated, and we’re starting to see that with cloud security automation. Our survey found IT and security professionals believe that automated remediation can provide significant value in ensuring security and compliance while improving efficiency.
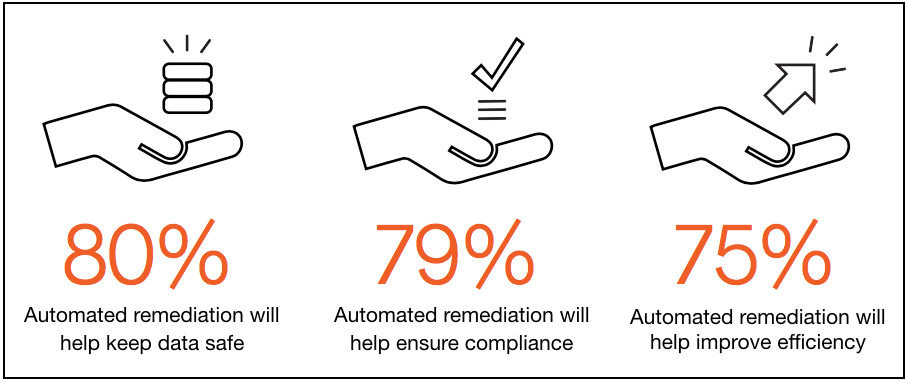
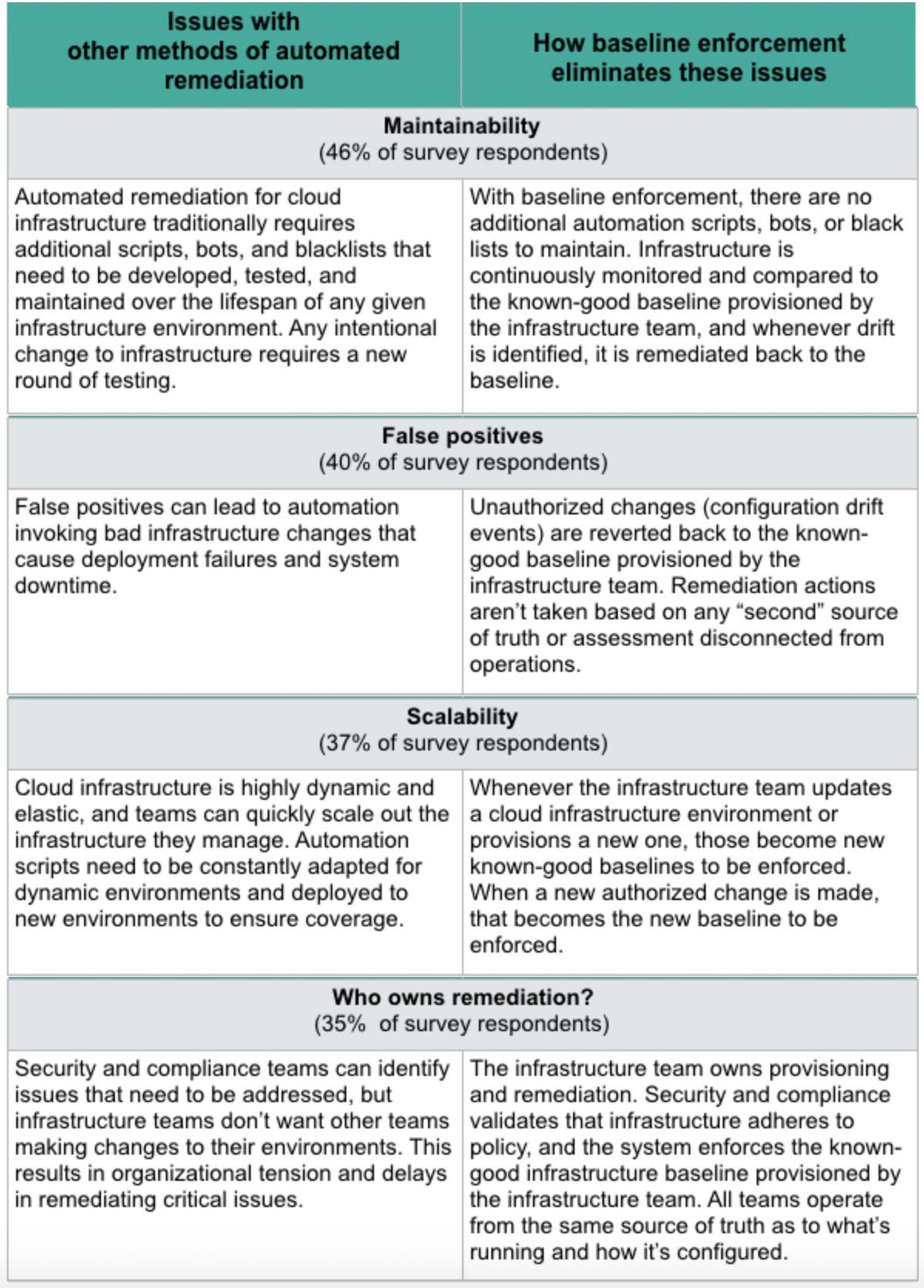
But there’s a big catch: automated remediation solutions are historically problematic, and our survey respondents told us so. Some of the primary issues cited include:
- False Positives. Anyone who uses a cloud security monitoring tool knows they can produce a lot of false positives, and automation solutions that act on such alerts are bound to invoke bad changes that can lead to system downtime events and deployment failures.
- Ownership and Management. Who owns and manages remediation? Infrastructure and development teams don’t like it when others move their cheese around, and for good reason. Security and compliance teams need to ensure that cloud infrastructure complies with relevant policy, but they don’t typically have the authority to invoke remediation of misconfiguration and other policy violations.
- Maintainability and scalability. The emerging automated remediation tools involve additional scripts, bots, and blacklists that need to be maintained, and they’re rarely tightly integrated with DevOps toolchains. Someone’s going to have to manage all this extra automation and ensure it’s being deployed properly and updated as needed. Maintaining multiple “sources of truth” for cloud infrastructure environments is never ideal.
Baseline enforcement is the answer to cloud misconfiguration
Rather than answering the challenge of cloud misconfiguration with more complexity, the solution should be simple: Establish a known-good infrastructure configuration baseline—and enforce it.
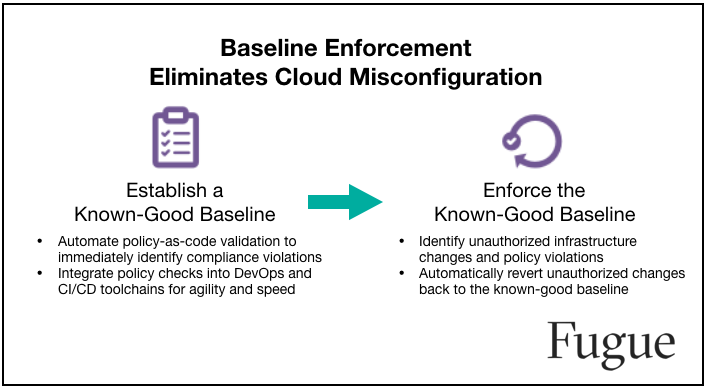
Infrastructure and development teams need to move fast, and security and compliance teams need to help them move fast without breaking important things (i.e., policy). With policy-as-code validation, security, compliance, and DevOps can work together efficiently to establish known-good infrastructure configuration baselines. Known-good baselines can be duplicated and shared, and automated validation checks can be integrated into DevOps and CI/CD toolchains.
Once infrastructure is provisioned, it is continuously monitored, and any unauthorized change (i.e., configuration drift) is automatically reverted back to the known-good baseline. Infrastructure and development teams benefit because they always know that what’s running is what they’ve declared, eliminating the risk of deployment failures due to configuration drift. Security and compliance benefits because they have assurance that infrastructure always adheres to policy.
Baseline enforcement prevents problems associated with other methods of automated remediation
Baseline enforcement with Fugue
Fugue employs baseline enforcement to provide assurance that cloud infrastructure is—and always remains—compliant with security and regulatory policies while protecting against breaches and downtime events due to configuration drift. Learn more here.
