
This week, Fugue announced support for AWS CloudFormation in Regula, the open-source policy engine for infrastructure as code (IaC). Regula has been gaining in popularity for performing pre-deployment security and compliance checks for Terraform, and we’re thrilled to extend Regula’s capabilities to address CloudFormation templates, including the Serverless Application Framework.
Regula is available on GitHub here, and as a Docker image on DockerHub here.
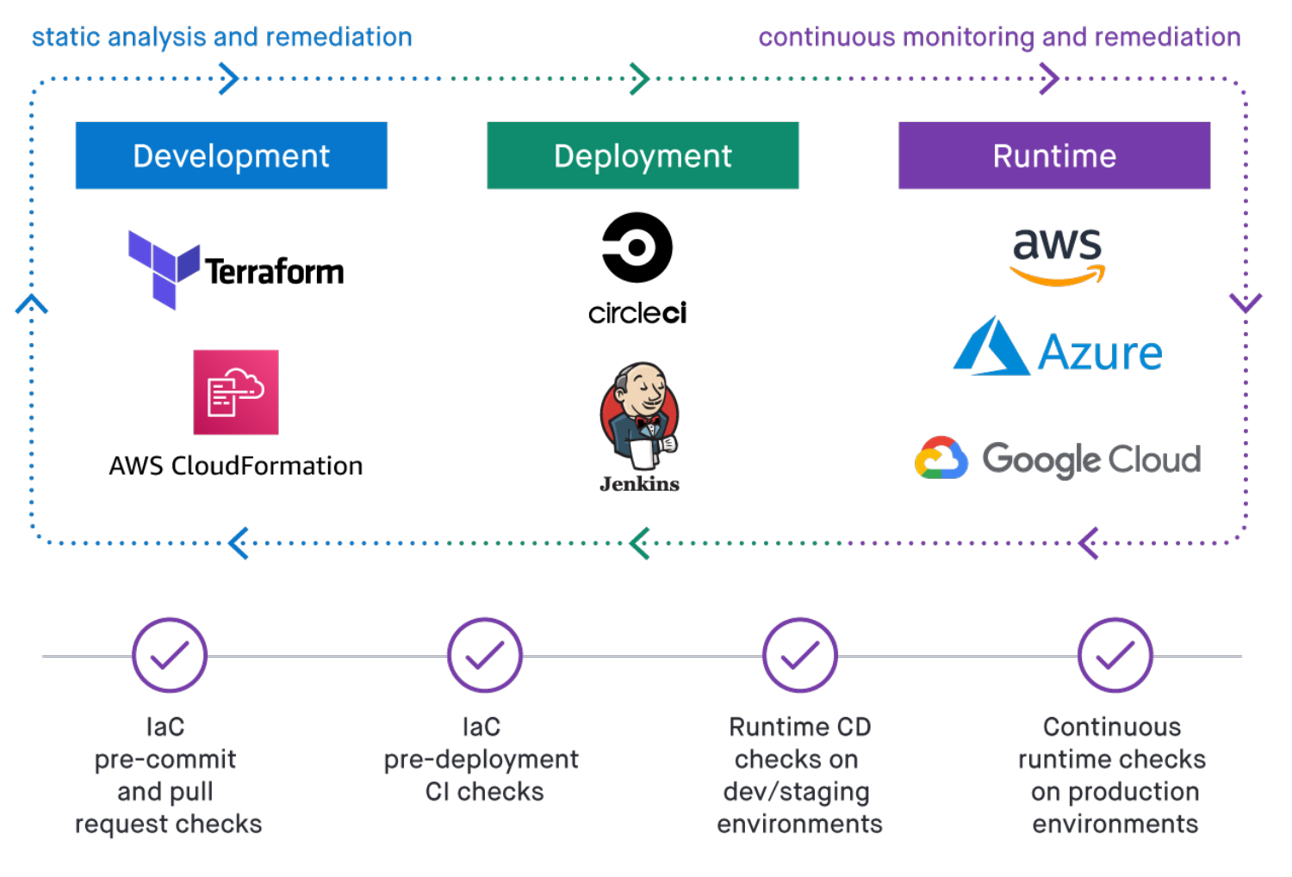
Our objective with Regula is to create the most flexible and powerful IaC policy engine that works across IaC tools and cloud platforms—and enables teams to use the same rules for IaC pre-deployment and cloud security post-deployment.
Meeting CIS AWS Foundations Benchmarks 1.2.0 and 1.3.0
Regula is the only IaC security tool for CloudFormation that helps teams meet the CIS AWS Foundations Benchmarks 1.2.0 and 1.3.0. Compliance can become a serious burden for any cloud engineering team, and the ability to check CloudFormation templates for compliance with CIS AWS Foundations Benchmarks can save a lot of time and avoid the risk of deploying non-compliant cloud infrastructure.
Detecting Multi-Resource Misconfiguration Vulnerabilities
Modern cloud attacks increasingly leverage multiple resource misconfigurations to gain access to cloud environments, move laterally, discover resources, and extract data. Often these attacks take advantage of IAM resource misconfigurations, many of which are impossible to detect in isolation. The security posture of cloud IAM resources must be assessed in the full context of the environment. [Watch our on-demand Cloud Security Masterclass on Locking Down the Security of AWS IAM]
Regula is the only IaC security tool for CloudFormation and Terraform that can catch vulnerabilities involving multiple resources—the kind that we’re seeing exploited more often in modern cloud attacks. If you aren’t catching these kinds of dangerous vulnerabilities in your IaC templates prior to deployment (or in the runtime post-deployment), your environment most likely contains them. Hackers are skilled at finding and exploiting your misconfiguration vulnerabilities, so you need to find them before they do, including multi-resource ones.
Integrating IaC Checks Into CI/CD
Teams that are using IaC to operate efficiently at scale in the cloud are more likely to be leveraging CI/CD pipelines, and Regula easily integrates into CI/CD. You can use Regula for pre-commit IaC checks and pull request feedback. And Regula doesn’t require any changes to how you deploy your cloud infrastructure. Fugue provides examples of Regula working with GitHub Actions for CI/CD.
Using the Same Rules for IaC and Running Cloud Infrastructure
Using different cloud infrastructure policy frameworks for IaC and the runtime is typical with other cloud security posture management approaches, and we don’t think that’s a good idea. Building and maintaining two sets of rules using different languages and frameworks designed to address the same resources at different stages of the cloud development lifecycle is a waste of time and resources. And reconciling the two is a Sisyphean task, creating risk of critical cloud security gaps.
While Regula works independently of Fugue, you can use Fugue to apply your Regula rules to check your cloud runtime environment for compliance and misconfigurations. Checking IaC for compliance is essential, but deployments and changes also occur outside of IaC and CI/CD and it’s important to continuously monitor for post-deployment misconfiguration and unwanted drift.
Securing the entire cloud development lifecycle (CDLC) with Fugue
While You’re Here
It takes just minutes to get up and running with Fugue and gain full visibility over your cloud environment and security posture across AWS, Microsoft Azure, and Google Cloud.
Our guarantee to you:
Fugue guarantees your success: Gain a complete, actionable view of your cloud environment and security posture in 15 minutes, and bring your cloud into compliance in 8 weeks under the Fugue FastTrack package. Learn more and get started.


