Today we released the Fugue Best Practices Framework to help software engineering teams identify and remediate the kinds of dangerous cloud resource misconfigurations used in recent data breaches that aren’t addressed by common compliance frameworks (see A Technical Analysis of the Capital One Cloud Misconfiguration Breach).
It takes just a few minutes to get up and running with Fugue and identify these misconfigurations. Using the Fugue Best Practices Framework in conjunction with a standard like CIS Foundations Benchmarks provides the most comprehensive protection against today’s advanced misconfiguration attacks.
Identify Advanced Cloud Misconfiguration Risks
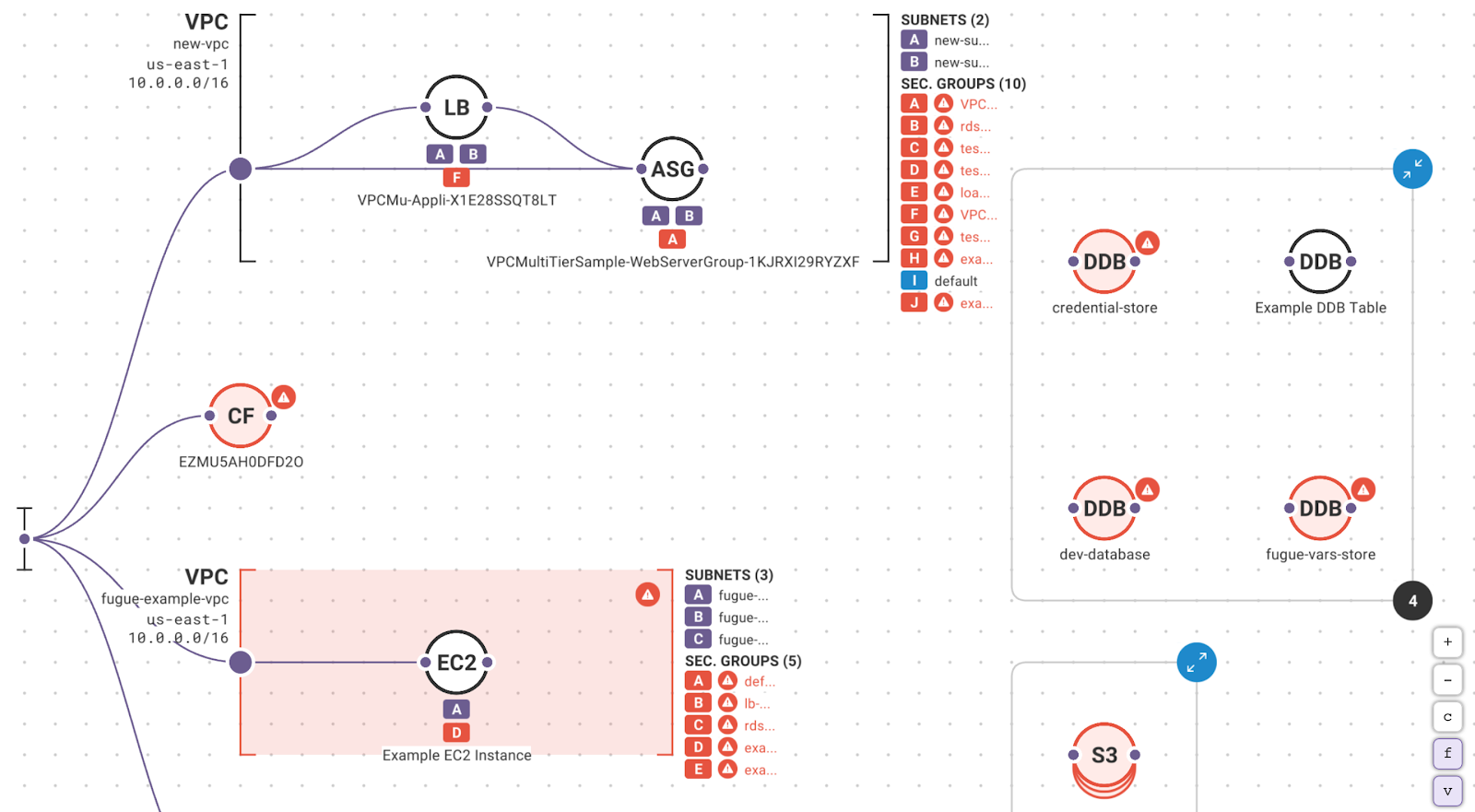
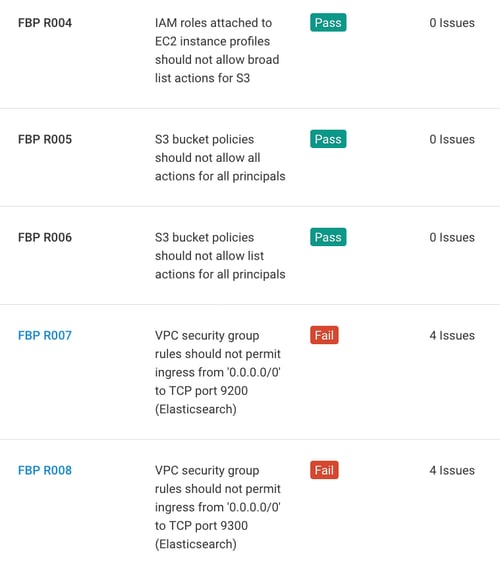
Fugue identifies critical cloud resource misconfigurations in your cloud environment that violate the Fugue Best Practices Framework. Scans can be triggered using Fugue’s API to integrate policy validations into developer workflows and CI/CD pipelines.
Fugue then continuously evaluates your environment to alert you on any changes that present new misconfiguration risks. You get detailed information on each misconfiguration to help you correct them.
The Fugue Best Practices Framework includes rules covering the following cloud vulnerabilities:
- Identity and Access Management (IAM) misconfigurations that can provide bad actors, including malicious insiders, with the ability to move laterally and discover resources to exploit
- Object storage policy misconfigurations that can be exploited in order to take data exfiltration actions
- Network security group rule misconfigurations that can enable malicious access via Elasticsearch, MongoDB, and other services
Fugue will continue to update the Fugue Best Practices Framework as new misconfiguration vulnerabilities and attack vectors are identified.
Enforce Baselines to Automatically Remediate Misconfiguration without Writing Code
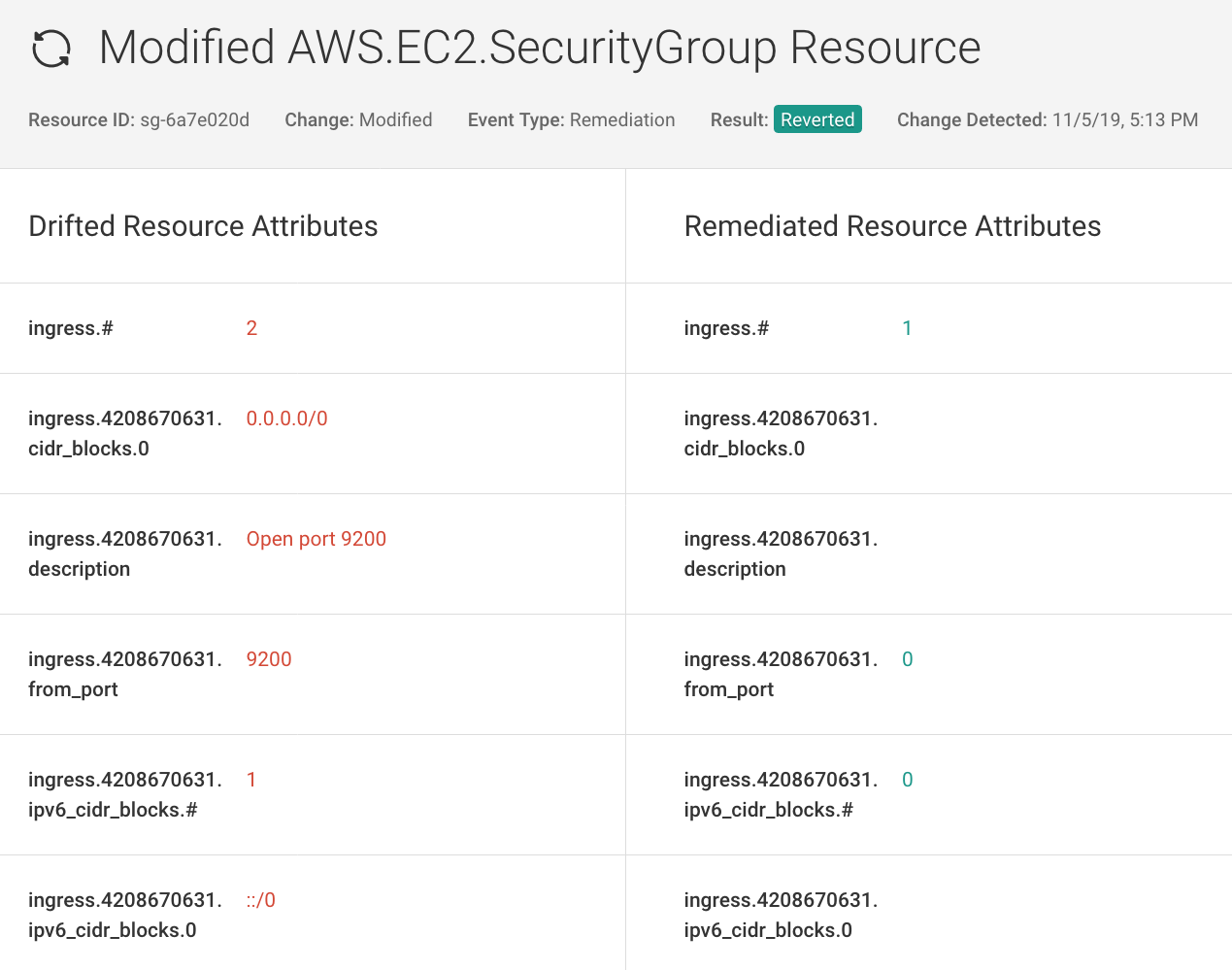
Use Fugue to baseline your cloud environment and monitor for changes that result in resource misconfigurations. For security-critical resources, employ baseline enforcement to correct any unauthorized change back to your established baseline without writing and managing automation scripts or bots.
Report on Your Cloud Security Posture
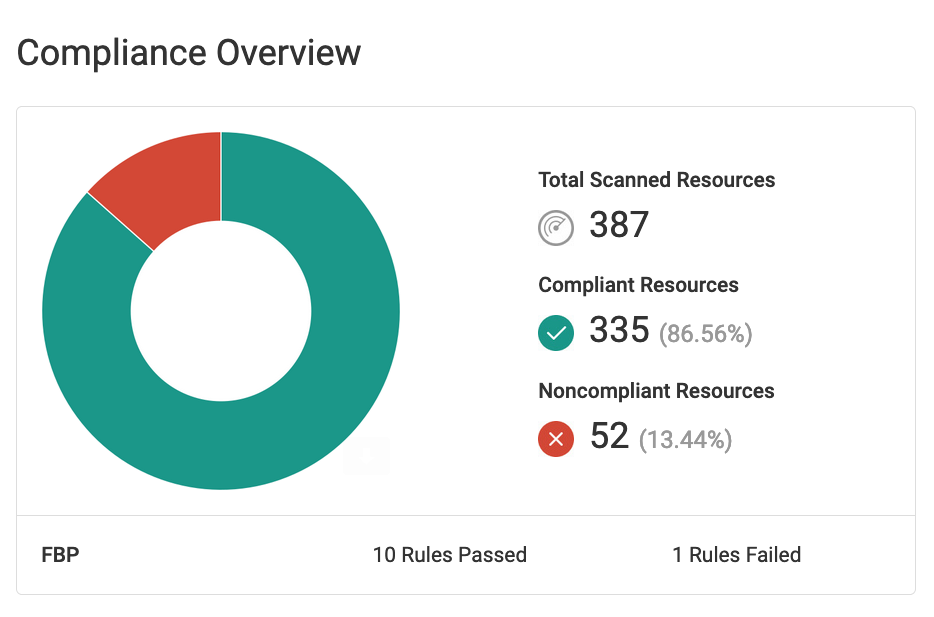
Fugue provides turnkey reporting on your cloud security posture with detailed dashboards and visualizations to track and monitor your cloud resources. Daily or weekly reports highlighting compliant and non-compliant resources can be emailed to executives or auditors to show proof of compliance.
In addition to the Fugue Best Practices Framework, Fugue makes it easy to create and deploy custom enterprise cloud infrastructure policies and supports out-of-the-box standards like CIS Foundations Benchmarks, GDPR, HIPAA, ISO 27001, NIST 800-53, PCI, and SOC 2.
While you’re here…
Fugue is cloud security for developers, by developers. We make tools that bake security into the entire system lifecycle on the cloud. We’d love to show you how.
With Fugue, you can:
- Get complete visibility into your cloud environment and configurations with dynamic visualization tools.
- Validate cloud infrastructure compliance for a number of policy frameworks like CIS Foundations Benchmark, HIPAA, PCI, SOC 2, NIST 800-53, ISO 27001, and GDPR.
- Protect against cloud misconfiguration with baseline enforcement to make security critical cloud infrastructure self-healing.
- Shift Left on cloud security and compliance with CI/CD integration to help your developers move fast and safely.
- Get continuous compliance visibility and reporting across your entire enterprise cloud footprint.
Give Fugue a try with a free trial or schedule a free half-hour workshop to learn how Fugue can help you manage your cloud security posture.