
Richard Park also contributed to this post.
The Apache Log4j vulnerability known as Log4Shell (CVE-2021-44228) is a serious vulnerability that allows an attacker to execute arbitrary code on any server running the popular Apache Log4j Java logging library. It has a CVSS score of 10, the highest possible value, and should be addressed immediately.
Version 2.15.0 of Log4j was released to mitigate Log4Shell, but the patch was determined to have its own vulnerability, CVE-2021-45046. Exploitations can lead to information leaks, remote code execution, and local code execution. Originally rated as a CVSS score of 3.7, or moderate severity, Apache states that the rating was modified to 9.0, critical severity.
Version 2.16.0 of Log4j fixes both vulnerabilities.
Fugue and Regula Are Not Impacted by Log4Shell
As explained on our security page, the Fugue platform and the open source tool Regula are not written with Java components and are therefore not impacted. Fugue’s reporting components are operated by Google Looker and were patched on December 13, 2021 for CVE-2021-44228 and on December 16, 2021 for CVE-2021-45046.
How Fugue Can Help Protect Against Log4Shell
Fugue has released a rule, available today, for AWS runtime and IaC repository environments (for Terraform) to confirm that AWS WAFv2 resources are using the AWS-managed rule group used to block request patterns associated with exploiting the Log4Shell vulnerability. Specifically, the Fugue rule checks for the presence of the Known Bad Inputs WAFv2 rule set (AWSManagedRulesKnownBadInputsRuleSet), which includes the Log4JRCE and Log4JRCE_ALL_HEADER WAFv2 rules.
Please note that in AWS, the Log4JRCE WAFv2 rule (and many others) only inspects the first 8 KB of the request body, so you may additionally want to ensure that the Core Rule Set (AWSManagedRulesCommonRuleSet) is also included, as the SizeRestrictions_BODY rule in that managed rule group verifies that the request body size is at most 8 KB.
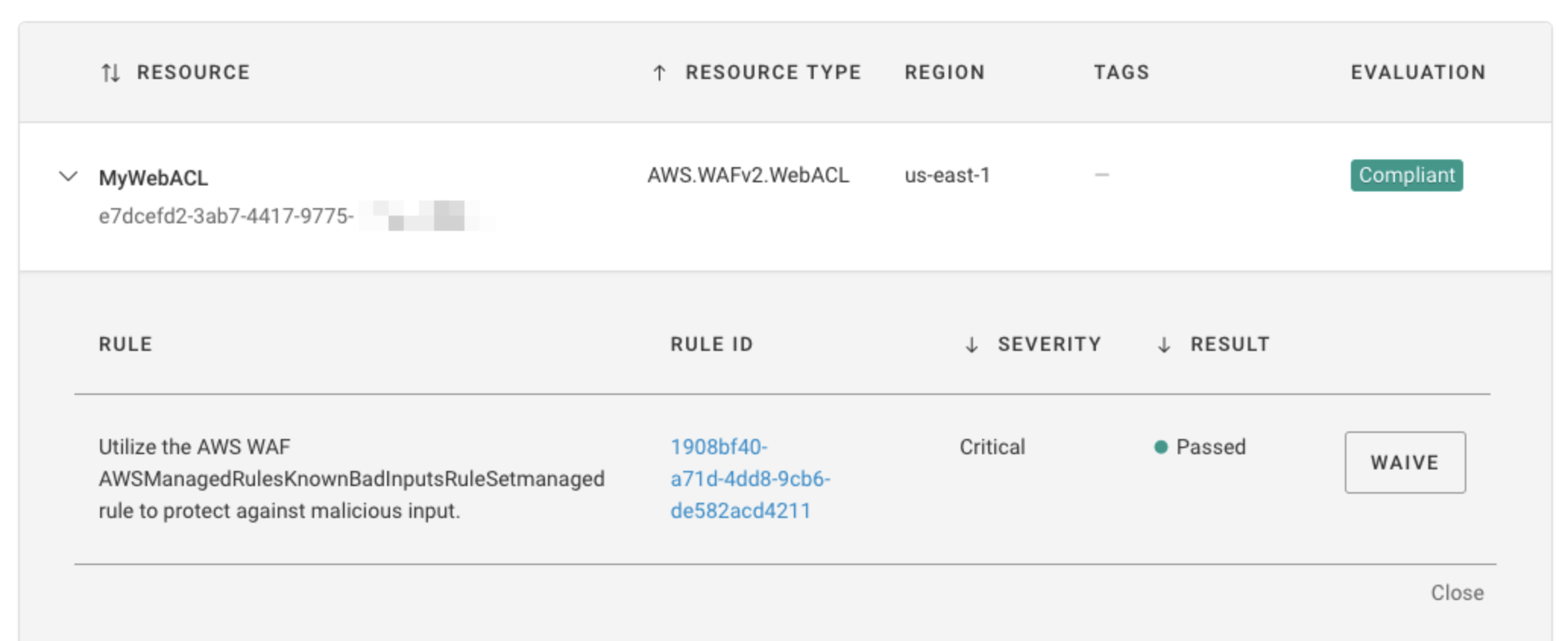
Enabling the Log4JRCE WAF rule in AWS
To learn how to use the AWS Console, AWS CLI, or Terraform to create a web ACL with the AWSManagedRulesKnownBadInputsRuleSet enabled, follow these remediation steps on the Fugue docs site.
Using Fugue to check an AWS runtime or Terraform environment
To apply the Fugue rule checking for Log4Shell protection to an AWS runtime or Terraform IaC environment:
- The Fugue tenant must have the rule enabled.
- Runtime only: the environment must have the Fugue Best Practices compliance family enabled.
- Runtime only: the environment must be configured to scan AWS WAFv2 resources.
Step 1: Enable the Fugue rule
The Fugue rule checking for the Log4JRCE and Log4JRCE_ALL_HEADER AWS WAFv2 rules is disabled by default. To enable the Fugue rule for your Fugue tenant, follow this link, or access the Rules page and search for FG_R00500. Then, toggle the "Enable rule" switch next to the rule.
Once the rule is enabled, it is applied to an environment on the next scan. A runtime environment must have the Fugue Best Practices compliance family enabled. The rule is automatically applied to AWS Terraform repository environments. You may kick off a scan immediately by selecting Actions > Start New Scan (for runtime environments) or executing regula run --sync --upload (for repository environments).
Step 2 (runtime only): Enable the Fugue Best Practices family
Fugue Best Practices is a policy framework designed to complement standards such as the CIS Foundations Benchmark to provide the most comprehensive protection against today's advanced misconfiguration attacks. To enable the Fugue Best Practices compliance family for an AWS runtime environment:
- Navigate to the environment in Fugue.
- Select the Actions drop-down menu.
- Select Edit Environment.
- Select the Compliance tab.
- Select Fugue Best Practices.
- Select Save Changes.
If FG_R00500 is enabled, it will be applied on the environment's next scan. You may kick off a scan immediately by selecting Actions > Start New Scan.
Step 3 (runtime only): Configure the environment to scan WAFv2 resources
If an AWS runtime environment is not configured to scan WAFv2 resource types, you can configure it by following the steps below:
- Navigate to the environment in Fugue.
- Select the Actions drop-down menu.
- Select Edit Environment.
- On the General tab, under Select Resource Types, search for "WAFv2" and check the boxes for the WAFv2 resources.
- IMPORTANT: Update your Fugue IAM role so Fugue has permission to scan the WAFv2 resources by following these steps in the Fugue docs.
Changes go into effect on the environment's next scan. You may kick off a scan immediately by selecting Actions > Start New Scan.
Using Regula to check Terraform IaC for Log4Shell protection
To use Regula as a stand-alone option to check AWS Terraform IaC for Log4Shell protection, install Regula according to your platform, then simply execute the following command in your Terraform project directory:
regula run
Regula will scan all of the infrastructure as code files in the current working directory and subdirectories, applying its library of rules. Rule FG_R00500 checks whether WAFv2 web ACLs include the AWSManagedRulesKnownBadInputsRuleSet managed rule group.
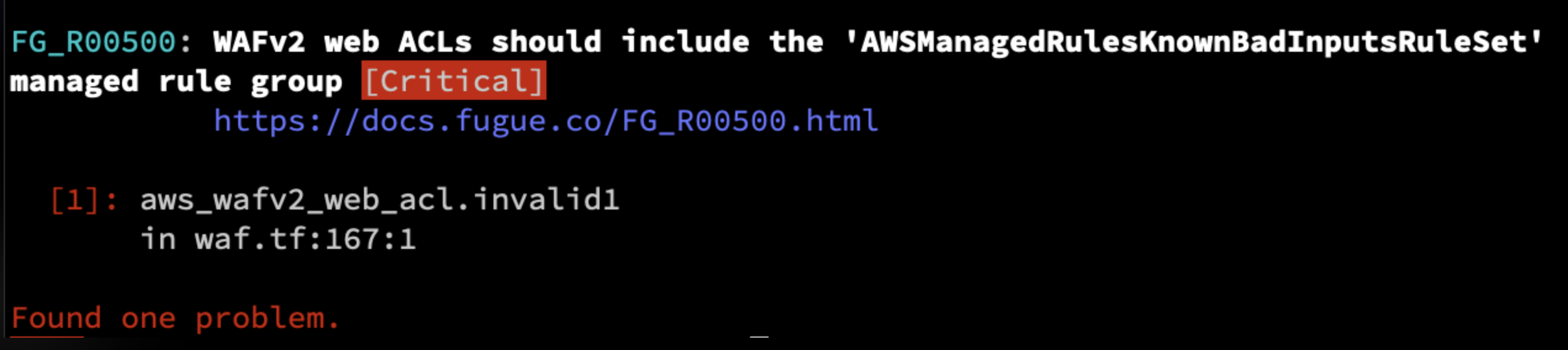
For more information about using Regula, see the Regula docs site.
