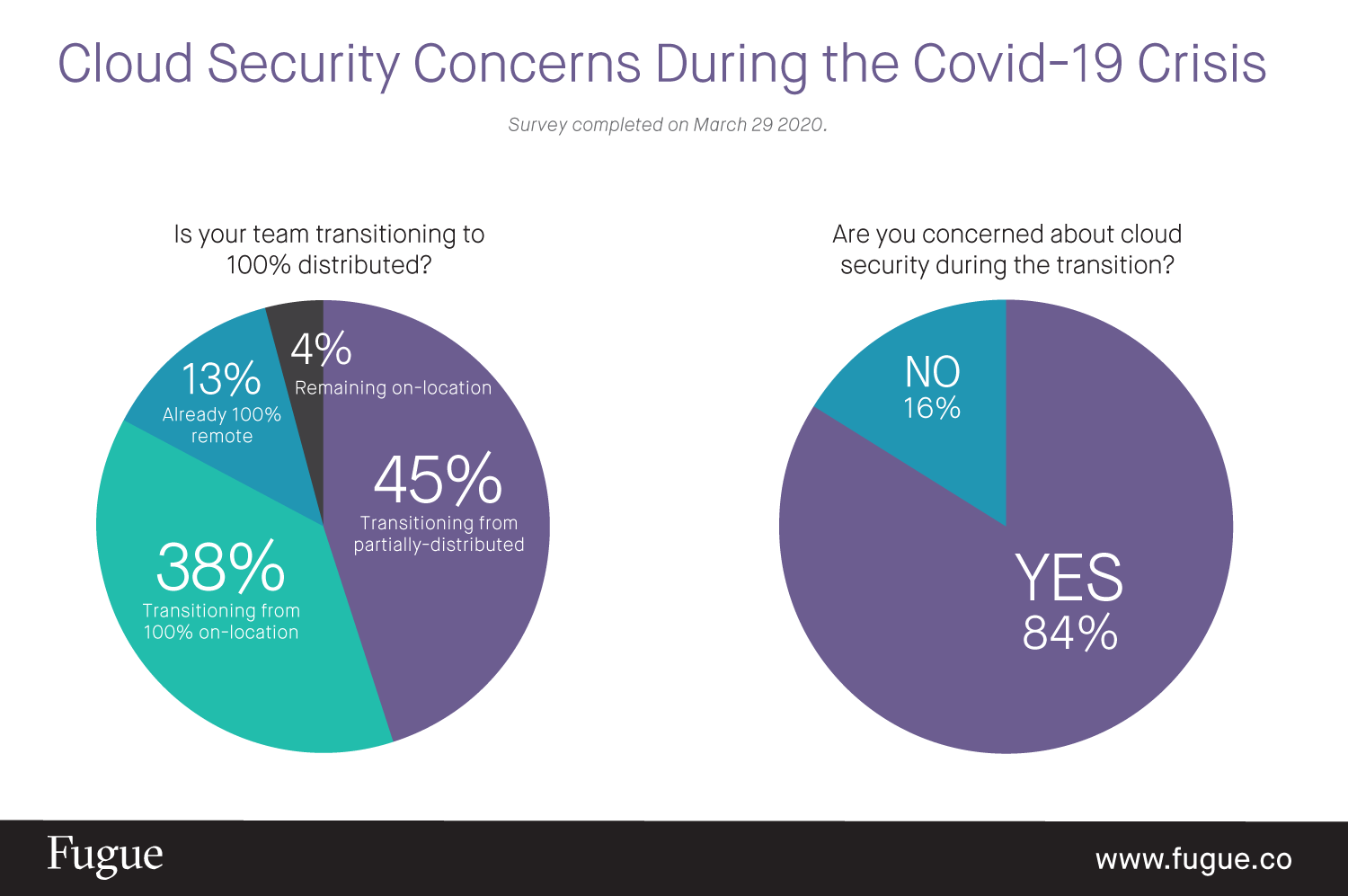
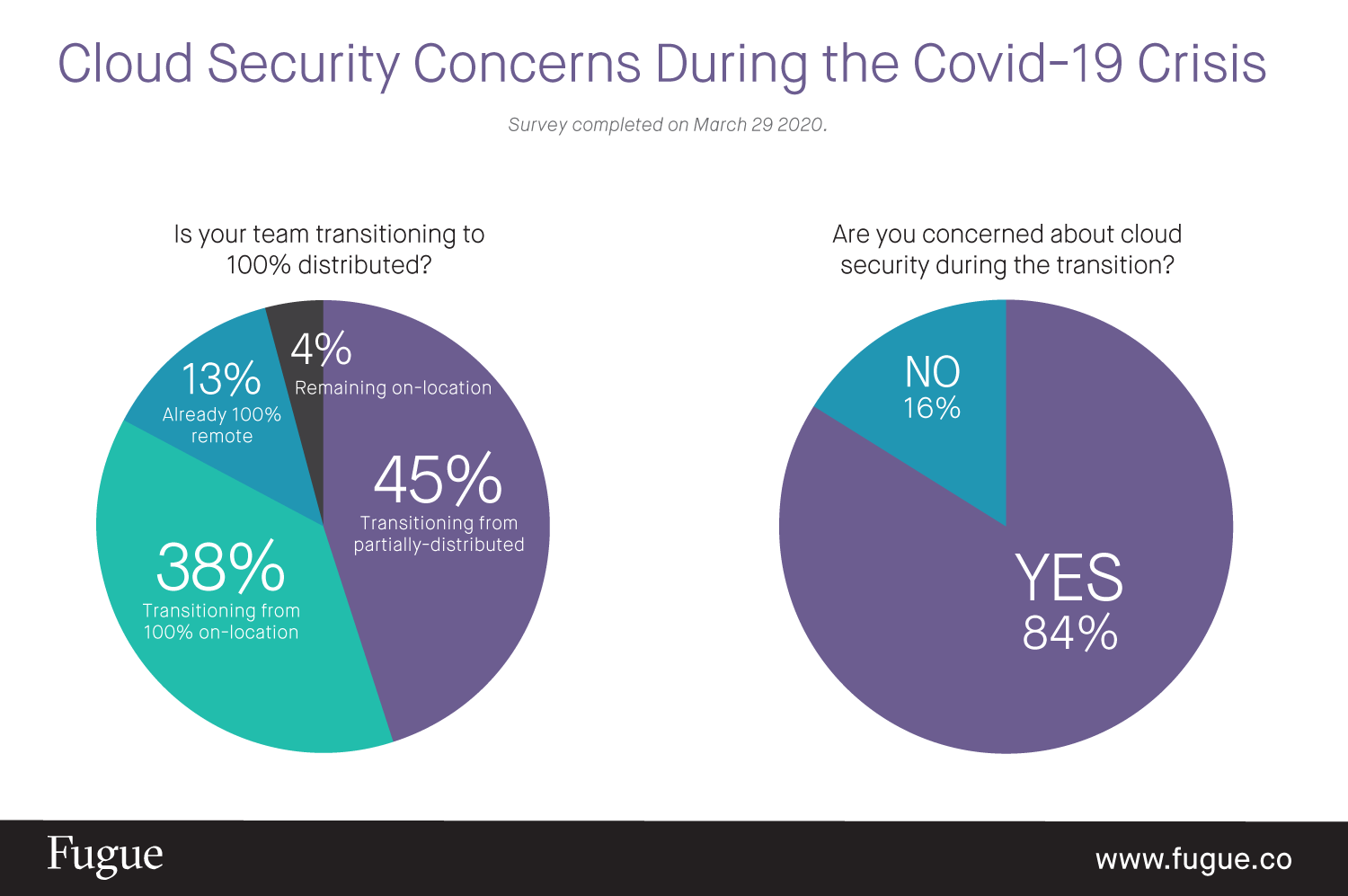
84% of IT professionals are worried about ensuring the security of cloud environments during the rapid transition to 100% distributed teams
Frederick, MD, April 13, 2020 – As a vast majority of companies make the rapid shift to work-from-home to stem the spread of COVID-19, a significant percentage of IT and cloud professionals are concerned about maintaining the security of their cloud environments during the transition. The findings are a part of the State of Cloud Security survey conducted by Fugue, the company putting engineers in command of cloud security.
The survey found that 96% of cloud engineering teams are now 100% distributed and working from home in response to the crisis, with 83% having completed the transition or in the process of doing so. Of those that are making the shift, 84% are concerned about new security vulnerabilities created during the swift adoption of new access policies, networks, and devices used for managing cloud infrastructure remotely.
“What our survey reveals is that cloud misconfiguration not only remains the number one cause of data breaches in the cloud, the rapid global shift to 100% distributed teams is creating new risks for organizations and opportunities for malicious actors,” said Phillip Merrick, CEO of Fugue. “Knowing your cloud infrastructure is secure at all times is already a major challenge for even the most sophisticated cloud customers, and the current crisis is compounding the problem.”
Download the full infographic PDF
84% are concerned they’ve already been hacked and don’t know it
Because cloud misconfiguration exploits can be so difficult to detect using traditional security analysis tools, even after the fact, 84% of IT professionals are concerned that their organization has already suffered a major cloud breach that they have yet to discover (39.7% highly concerned; 44.3% somewhat concerned). 28% state that they’ve already suffered a critical cloud data breach that they are aware of.
In addition, 92% are worried that their organization is vulnerable to a major cloud misconfiguration-related data breach (47.3% highly concerned; 44.3% somewhat concerned). Over the next year, 33% believe cloud misconfigurations will increase and 43% believe the rate of misconfiguration will stay the same. Only 24% believe cloud misconfigurations will decrease at their organization.
Causes of cloud misconfiguration: Lack of awareness, controls, and oversight
Preventing cloud misconfiguration remains a significant challenge for cloud engineering and security teams. Every team operating on cloud has a misconfiguration problem, with 73% citing more than 10 incidents per day, 36% experiencing more than 100 per day, and 10% suffering more than 500 per day. 3% had no idea what their misconfiguration rate is.
The top causes of cloud misconfiguration cited are a lack of awareness of cloud security and policies (52%), a lack of adequate controls and oversight (49%), too many cloud APIs and interfaces to adequately govern (43%), and negligent insider behavior (32%). Only 31% of teams are using open source policy-as-code tooling to prevent misconfiguration from happening, while 39% still rely on manual reviews before deployment.
Respondents cited a number of critical misconfiguration events they’ve suffered, including object storage breaches (32%), unauthorized traffic to a virtual server instance (28%), unauthorized access to database services (24%), overly-broad Identity and Access Management permissions (24%), unauthorized user logins (24%), and unauthorized API calls (25%). Cloud misconfiguration was also cited as the cause of system downtime events (39%) and compliance violation events (34%).
73% still rely on manual processes to defend against automated misconfiguration threats
While malicious actors use automation tools to scan the internet to find cloud misconfigurations within minutes of their inception, most cloud teams still rely on slow, manual processes to address the problem. 73% use manual remediation once alerting or log analysis tools identify potential issues, and only 39% have put some automated remediation in place. 40% of cloud teams conduct manual audits of cloud environments to identify misconfiguration.
A reliance on manual approaches to managing cloud misconfiguration creates new problems, including human error in missing or miscategorizing critical misconfigurations (46%) and when remediating them (45%). 43% cite difficulties in training team members to correctly identify and remediate misconfiguration, and 39% face challenges in hiring enough cloud security experts. Issues such as false positives (31%) and alert fatigue (27%) were also listed as problems teams have encountered.
The metric for measuring the effectiveness of cloud misconfiguration management is Mean Time to Remediation (MTTR), and 55% think their ideal MTTR should be under one hour, with 20% saying it should be under 15 minutes. However, 33% cited an actual MTTR of up to one day, and 15% said their MTTR is between one day and one week. 3% said their MTTR is longer than one week.
Managing cloud misconfiguration is costly
With cloud misconfiguration rates at such high levels and a widespread reliance on manual processes to manage it, the costs are predictably high for cloud customers. 49% of cloud engineering and security teams are devoting more than 50 man hours per week managing cloud misconfiguration, with 20% investing more than 100 hours on the problem.
When asked what they need to more effectively and efficiently manage cloud misconfiguration, 95% said tooling to automatically detect and remediate misconfiguration events would be valuable (72% very valuable; 23% somewhat valuable). Others cited the need for better visibility into cloud infrastructure (30%), timely notifications on dangerous changes (i.e., “drift”) and misconfiguration (28%), and improved reporting to help prioritize remediation efforts (8%).
What is Cloud Misconfiguration?
Cloud security is about preventing the misconfiguration of cloud resources such as virtual servers, networks, and Identity and Access Management (IAM) services. Malicious actors exploit cloud misconfiguration to gain access to cloud environments, discover resources, and extract data. The National Security Agency states that “misconfiguration of cloud resources remains the most prevalent cloud vulnerability and can be exploited to access cloud data and services.”
With the cloud, there’s no perimeter that can be defended, exploits typically don’t traverse traditional networks, and legacy security tools generally aren’t effective. Because developers continuously build and modify their cloud infrastructure, the attack surface is highly fluid and expanding rapidly. Organizations widely recognized as cloud security leaders can fall victim to their own cloud misconfiguration mistakes.
With the Shared Responsibility Model, cloud providers such as Amazon Web Services, Microsoft Azure, and Google Cloud Platform are responsible for the “security of the cloud,” and the customer is responsible for the “security in the cloud.” While cloud providers can educate and alert their customers about potentially risky misconfigurations and good security practices, they can’t prevent their customers from making misconfiguration mistakes.
About this Survey
Fugue partnered with Propeller Insights to survey 300 IT, cloud, and security professionals, including DevOps engineers, cloud architects, security engineers, site reliability engineers (SREs), DevSecOps engineers, and application developers. Professionals from companies representing a variety of industries that use Amazon Web Services, Microsoft Azure, and Google Cloud Platform for cloud computing were surveyed.
About Fugue
Fugue puts engineers in command of enterprise cloud security with tools to prove compliance, build security into cloud development, and stay safe by eliminating cloud misconfiguration. Fugue provides one-click reporting for CIS Foundations Benchmarks, GDPR, HIPAA, ISO 27001, NIST 800-53, PCI, and SOC 2. Customers such as AT&T, SAP NS2, and A+E Networks trust Fugue to protect their cloud environments. Fugue’s investors include New Enterprise Associates, Future Fund, and In-Q-Tel (IQT). Fugue is an AWS Advanced Technology Partner and has twice been named a CyberSecurity Breakthrough Award winner and a Gartner Cool Vendor in Cloud Computing. Fugue offers Enterprise and Team plans under a 30-day free trial, and the free Fugue Developer plan for individual engineers. To learn more, visit www.fugue.co.
Media Contact
Rachel Kaseroff
415-341-5625





