Here are four common hurdles nearly every organization using the cloud encounters:
- Inconsistent enforcement of regulatory compliance policies (PCI, HIPAA, NIST 800-53)
- Uneven use of internal governance policies
- Uncontrolled shadow IT, ad hoc automation, and tooling sprawl
- Increased demand for cloud expertise
Viewed from a higher level, companies using the cloud need to see all resources running across environments, accounts, and teams. Otherwise it’s impossible to know for sure if these resources are compliant with relevant rules and standardized for efficiency, scale, and speed. That’s a lot of potentially wasted cloud spend, not to mention your team’s wasted time. But while the cloud brings new risks, it also offers the opportunity to achieve a level of security and compliance that simply wasn’t possible before.
Cloud vs. Datacenter
Perhaps the biggest conflict we see in the marketplace pits the cloud against the datacenter. The two systems are almost always clashing at the enterprise level as organizations try to go fast with their cloud infrastructure while simultaneously pulling their legacy systems along. Actually, dragging their legacy systems along is often more accurate.
The cloud is radically different than the datacenter. In the datacenter, change typically happens more slowly. This is partly due to the difficulty of scaling hardware up and down at will and partly due to the longer release cycles for enterprise applications—although modern DevOps approaches in the datacenter are changing the latter.
Conversely, change is constant in the cloud. Release frequency is often hours or days. Using service-oriented architectures (SOA) and microservices (via machine images or containers or serverless functions) means there is vastly more “stuff” to manage and track. And the fact that provisioning cloud infrastructure and changing configurations is just an API call away only compounds the governance challenge.
In today’s hypercompetitive landscape, speed of innovation is critical for survival. Without corrective measures, the slow enterprise will decline. Those manual security and compliance reviews in the datacenter? They’re now choke points in the delivery cycle and they imperil the pace of enterprise innovation. Manual reviews are also prone to human error and can allow critical misconfigurations to go undetected.
Security and Compliance in the Cloud
Headlines are full of stories about cloud misconfiguration exposure incidents. If you approach the cloud like a remote datacenter—as many organizations do—you’ll lose out on the benefits of speed, agility, and savings. That approach also puts your organization at risk for common misconfiguration exposures, drift events, and related data leaks and breaches. Good times! However, when provisioned correctly and fully automated, the cloud can be much more secure than an on-premise datacenter. It provides all the building blocks to create extremely secure and compliant infrastructure.
Perhaps the biggest security advantage the cloud has over traditional on-premise datacenters is easier automation. Because the cloud is API-driven and fully programmable, everything can be automated with less overhead. Doing anything short of full automation is likely hampering your organization’s agility, wasting money, slowing innovation, and introducing risk.
With this in mind, let’s turn to the key question.
How Can You Achieve Cloud Infrastructure Governance?
Cloud infrastructure governance ensures that cloud infrastructure is configured according to a set of controls and policies (internal and external)—it includes best practices, organizational standards, and formal regulations. It is a system whereby only resources that adhere to established policies and controls can ever be created, and compliance is assured for the entire lifecycle of a given resource.
Principles of Cloud Infrastructure Governance
We’ve described what cloud infrastructure governance is, but what does that really mean? To achieve it, here are two key principles to adhere to:
-
Automation is the key to success: Manual processes carried over from the datacenter, such as approvals and audits, are slow and prone to human error, which means there’s a significant risk of compliance violations and data breaches. You cannot innovate at velocity if you have manual gates.
-
Governance automation must happen at the cloud service provider (CSP) API layer: The cloud API is at the intersection between your operations and the cloud provider. Fugue (or whatever infrastructure governance solution you use) must become the new gatekeeper. See all of the recent S3 misconfiguration breaches as proof of what happens without one.
Policy-as-Code ... the Only Way to Automate for Scale
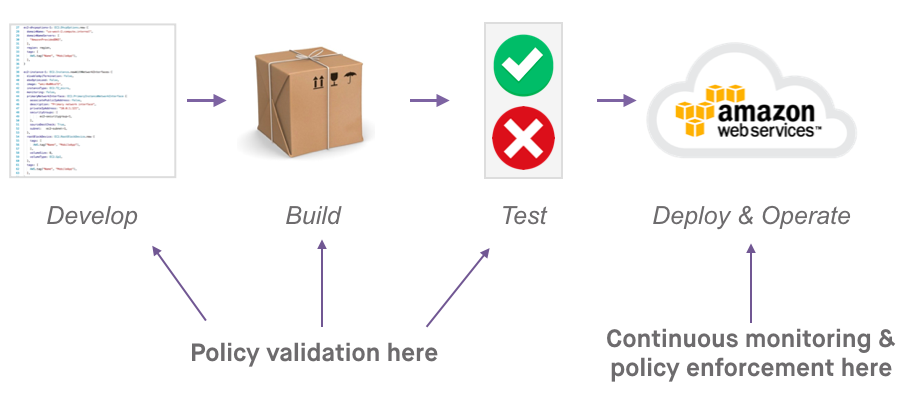
In order to automate cloud infrastructure governance, your compliance and security policies must be expressed as source-controlled policy-as-code—there’s no other effective way to automate for scale. The manual checklists and binders of policy documents are insufficient to govern ephemeral, fast-changing cloud infrastructure.
Policy-as-code must be expressed in the same language as infrastructure-as-code in order to provide validation and enforcement across the entire infrastructure lifecycle: design → provisioning → ongoing operations. If it’s in a different language, you are now managing two tools (i.e., two sources of truth), and you will always have the burden of keeping the two in sync. Most likely, you’ll be applying policy at a single point in the infrastructure lifecycle, such as at provisioning, but not in design time or for running infrastructure.
Here’s How to Solve the Cloud Infrastructure Governance Problem
Here are some battle-tested protocols that will empower your company to move fast in the cloud without compromising security, compliance, or control:
-
Make policy compliance a requirement for provisioning: If all infrastructure provisioning and change goes through an automated channel, you can enforce compliance. At Fugue, if it doesn’t comply, it doesn’t provision. A policy violation should “break the build.” Some solutions, like Fugue, provide a language compiler that empowers engineers to validate their infrastructure code against policy-as-code in design time and fix errors fast before attempting to provision.
-
Have zero tolerance for configuration drift: It’s critical to ensure that no infrastructure that violates policy can ever be provisioned. However, if you don’t address configuration drift for running infrastructure, you’re inviting misconfiguration exposures and post-provisioning policy violations.
-
Don’t rely solely on monitoring and alerting tools: Using those tools is how policy violations and configuration drift are typically addressed, but they aren’t good enough for constantly changing cloud environments! Some of the problems with legacy tooling include alert fatigue, false positives, and a Mean Time To Remediation (MTTR) measured in hours or days. In today's world, where bots constantly probe networks to find and exploit misconfigurations, remediation needs to occur in real time, period.
-
Remove human intervention from the process: Combing through alerts to identify those that need attention wastes valuable engineering resources, not to mention that, once the “real” alerts are identified, you have to manually remediate all the issues! Instead, any unauthorized change, configuration drift, or policy violation must be identified and automatically remediated within minutes. Human intervention must be removed from the process.
Build Freeways Instead of Toll Booths
If you’re working at an enterprise scale organization operating in the cloud, you likely have cloud workloads running in multiple cloud accounts across multiple regions. Additionally, you likely have several different teams—application, infrastructure, compliance and security—involved in cloud operations. If you want to move fast and innovate while ensuring compliance, then your operating environment must include role-based-access controls to regulate who can create, change, and access cloud resources. Further, your cloud infrastructure governance solution must provide control and visibility across everything you have running at all times.
Cloud infrastructure governance shouldn't be a gating function that slows down innovation, as security and compliance practices have a long history of doing. It should be more like an innovation freeway rather than a resource- and time-consuming tollbooth. Build freeways. You’ll have an easier journey down the road.
