Today, we announced Fugue Developer, a free tier designed for individual engineers to build and maintain secure cloud infrastructure in highly dynamic and regulated cloud environments. Get started here and you'll have a visualization of your AWS or Azure environment in minutes.
Software developers now own the security of their cloud infrastructure, and that’s who Fugue Developer serves. Fugue Developer provides tools to visualize cloud infrastructure environments, detect resource misconfiguration and policy violations, report on compliance, and understand infrastructure change.
We're excited about making Fugue Developer available to you for free. Let’s take a closer look.
Cloud Visualization: Discovery with Fugue Developer
Keeping track of the cloud resources you have running and how they’re configured across accounts and regions, involves countless hours clicking through consoles, updating spreadsheets, and manually creating infrastructure diagrams. Corey Quinn once said (and I paraphrase): “the only way to see everything you have running in your AWS account is to look at your AWS bill.”
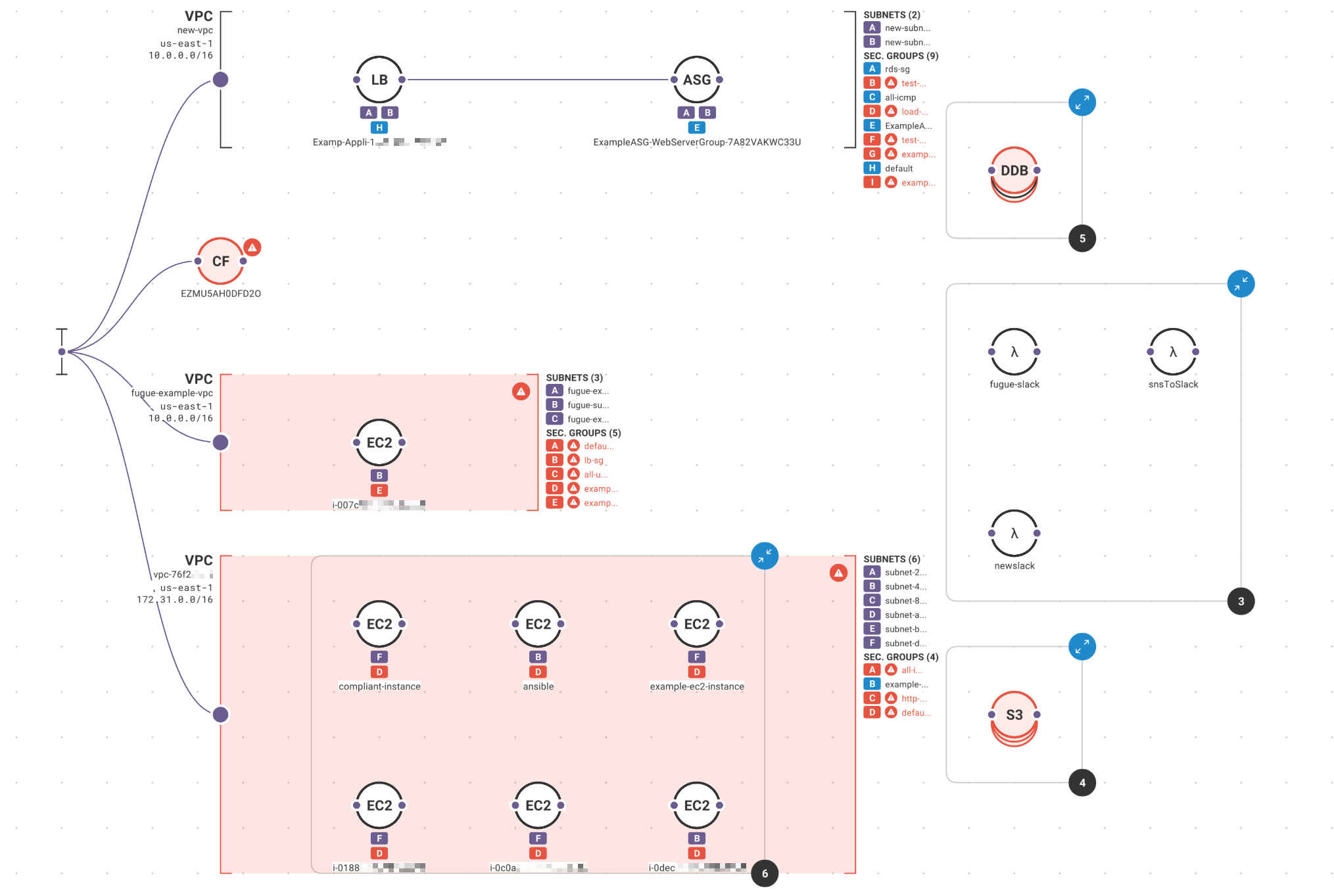
Fugue Developer changes this by taking a snapshot of your cloud environment, building a complete model of the configuration state, and generating dynamic visualizations so you can see what you have running and the relationships between resources. Generate new visualizations on a schedule and use the Fugue API to kick them off with each deployment. No more manually auditing cloud environments or wasting time with diagramming tools.
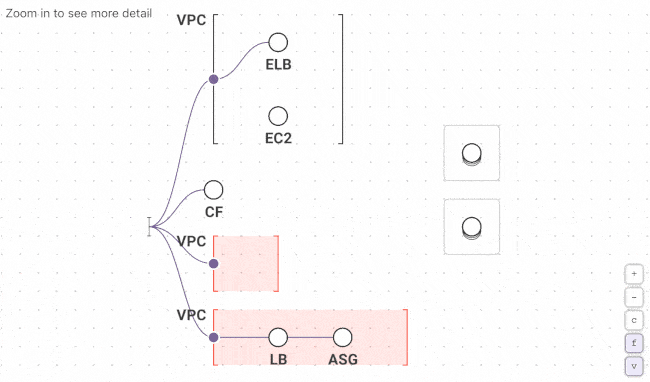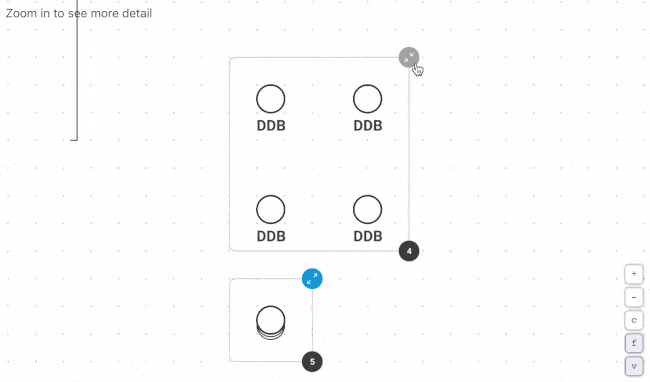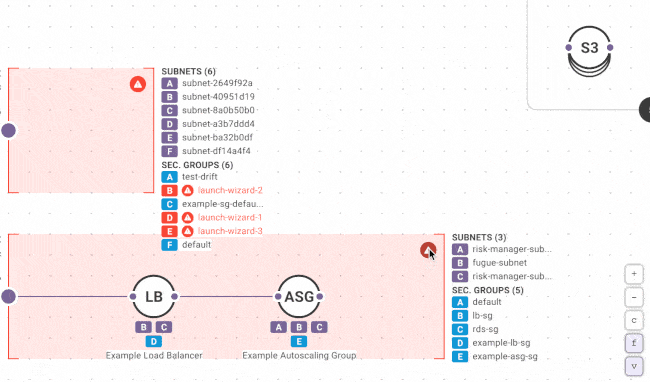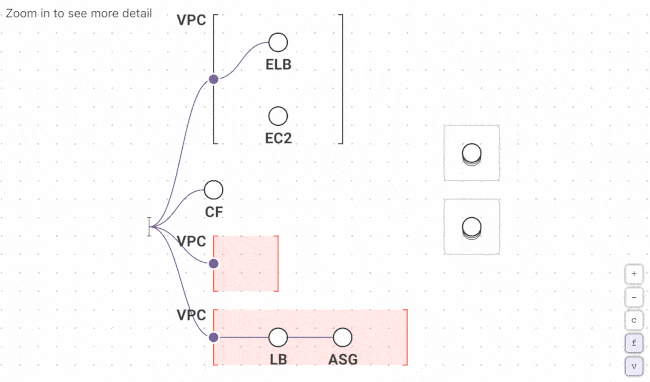
First time Fugue users often discover orphaned resources, redundant VPCs and security groups, crypto-mining instances, and other critical cloud infrastructure issues that become readily apparent when visualized.
Cloud Compliance: Policy as Code with Fugue Developer
Cloud infrastructure environments are too vast, complex, and dynamic to address with traditional security and compliance approaches such as manual audits, checklists, and scan/alert tools. The tradeoffs between agility and security in the cloud usually results in neither. And those in a position to make a difference—software developers—are left hamstrung and frustrated.
Policy as code is the answer, and Fugue Developer uses the open source Open Policy Agent (OPA) and Rego policy language—not some limited proprietary language. Custom cloud infrastructure policy with Fugue Developer is extremely flexible and scalable, and creating policies is straightforward. And we just open sourced the Fugue Rego Toolkit (Fregot) to help developers easily evaluate Rego expressions, debug code, and test policies.
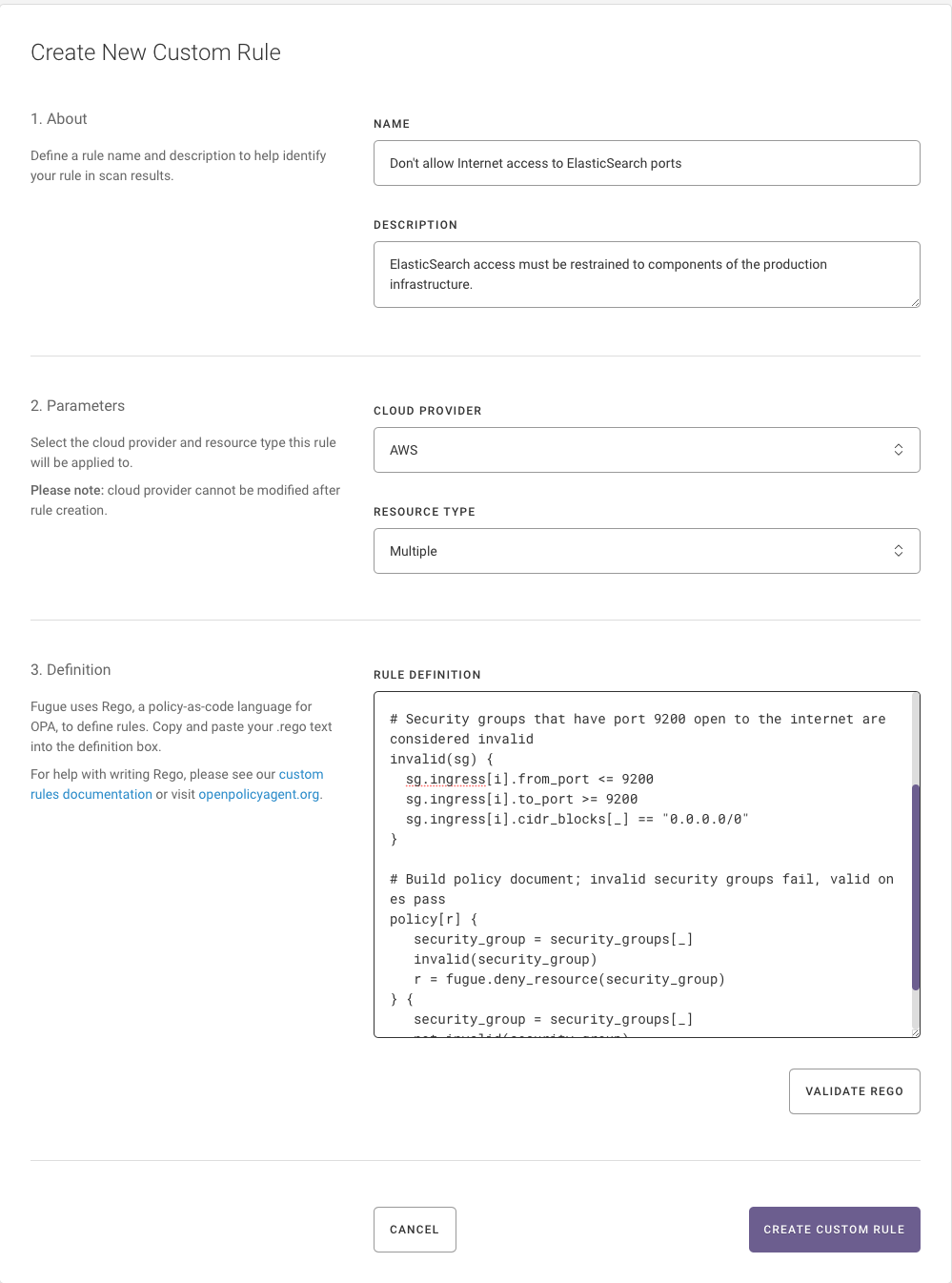
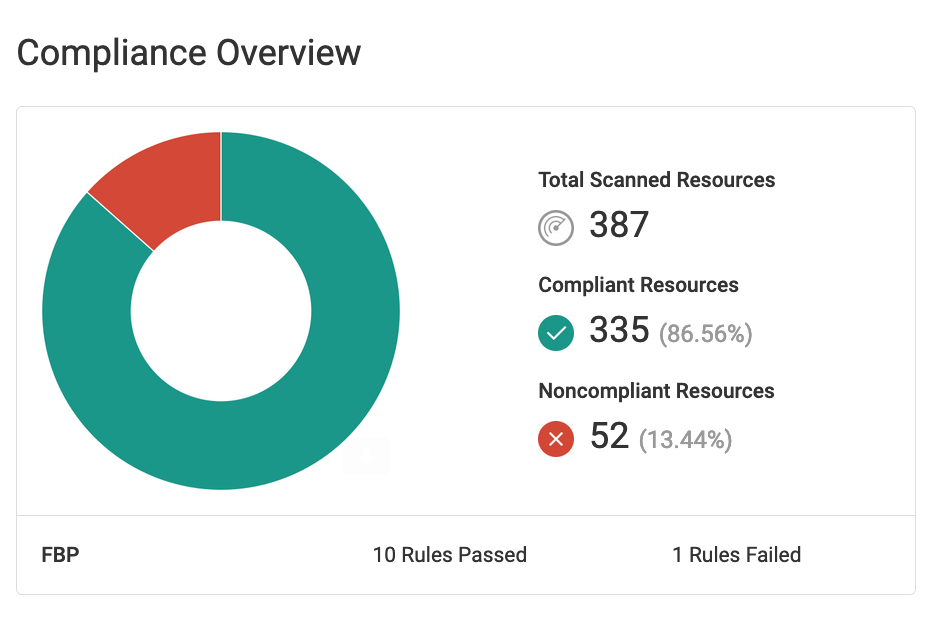
Fugue Developer also comes with support for CIS Foundations Benchmarks for Amazon Web Services (AWS) and Microsoft Azure out of the box. And you can apply the Fugue Best Practices Framework to your environment to detect advanced cloud misconfiguration vulnerabilities that industry standards such as CIS won’t catch.
Use Fugue Developer to create daily compliance reports for your cloud environment.
Understanding the Impact of Cloud Change with Fugue Developer
In the cloud, change is the only constant. And all that change brings constant risk of resource misconfiguration and policy violations. As important as it is to prevent misconfiguration before it gets deployed, it’s equally important to detect dangerous changes when they occur so you can correct them before they’re exploited.
Use Fugue Developer to snapshot your cloud environment before and after each deployment to check that desired changes occurred as intended, and nothing else. Fugue Developer will let you know if changes violated policy, and the feedback Fugue provides helps you correct them quickly and move on. Use Fugue’s API or CLI to automate snapshots and policy validations in each stage of the software development lifecycle (SDLC), such as dev, test, staging, and prod.
Fugue’s visualization tool comes in handy when checking that changes made to your environment are good ones. No more spelunking through logs and cloud consoles to validate your deployments.
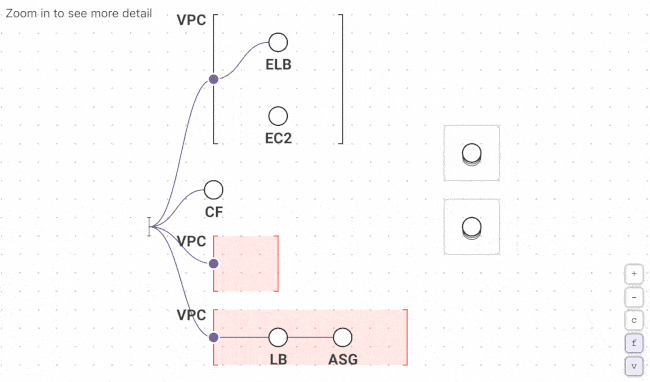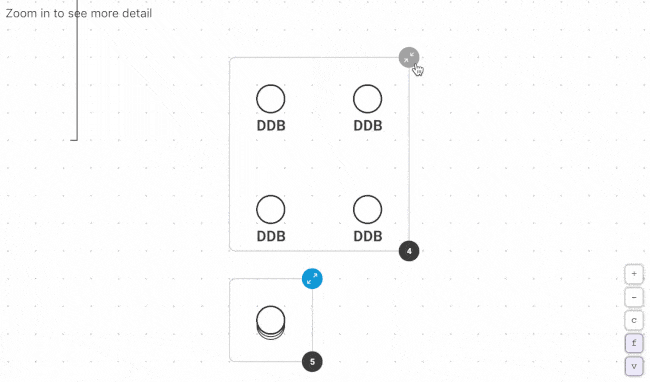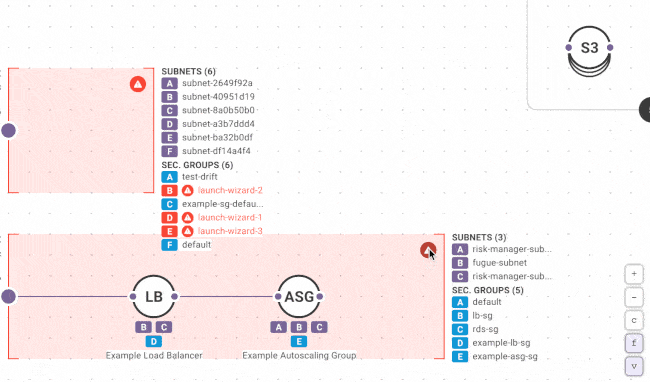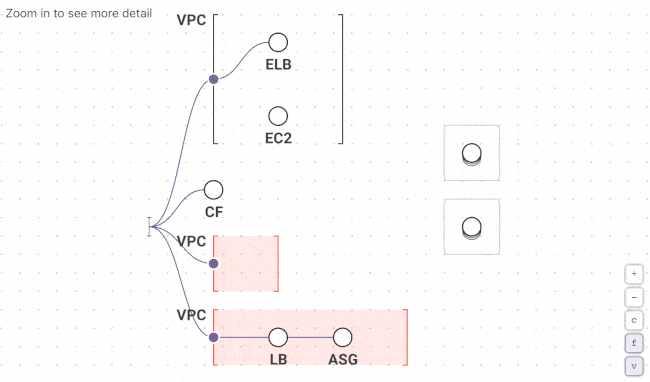
While we’d all prefer that change only occurs via our approved and automated channel (i.e. CI/CD pipeline or deployment tool), that’s no one’s reality. New Fugue users are often surprised to discover just how much change happens to their environment out of band. Fugue detects changes with each snapshot (which can be scheduled or triggered via the Fugue API or CLI) so you can quickly identify misconfiguration vulnerabilities and correct them.
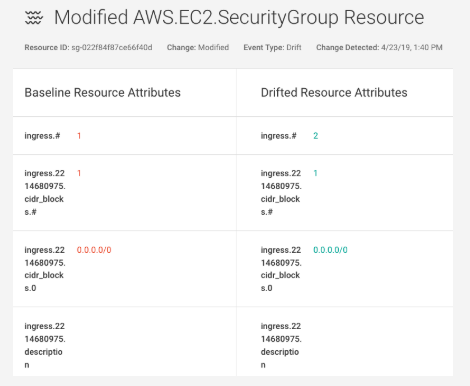
To protect security-critical cloud resources, use Fugue Developer to detect and remediate unauthorized changes (i.e. “drift”) without having to code and manage a bag of scripts or bots. Simply create a Fugue environment containing your critical resources that shouldn’t change out-of-band (e.g. VPCs, security groups; S3 buckets), baseline the environment, and tell Fugue to enforce the baseline. Fugue reverts any change back to your baseline when it detects drift.
Get Fugue Developer Now. It’s Free Forever.
Fugue Developer is available now for individual engineers here.
It takes just minutes to get up and running with Fugue Developer and you’ll have a full picture of your cloud infrastructure environment and security posture.
You'll receive a 30-day free trial of Fugue Enterprise, after which you can choose to purchase Fugue Enterprise or transition to Fugue Developer. Fugue Enterprise supports unlimited users and environments, and provides additional out-of-the-box support for NIST 800-53, PCI, HIPAA, SOC 2, GDPR, and ISO 27001.