All humans make mistakes and some of those mistakes could lead to security breaches. According to Gartner, through 2023 at least 99% of cloud security failures will be the customer’s fault. Many of these successful cyber-attacks will be a result of hackers preying on the vulnerabilities of human weakness to successfully gain access to an organization’s infrastructure and networks wreaking havoc and damage.
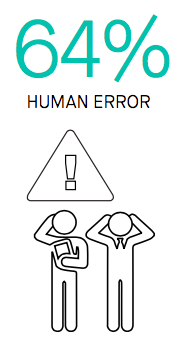
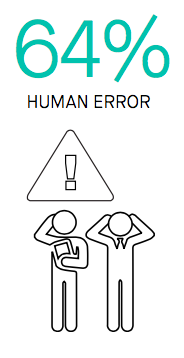
One of the most common forms of human errors that could easily expose your organization to security risk is cloud misconfiguration that occurs after deployment. Fugue has found that 64% of organizations said that human error was the main cause of misconfiguration. Whether it was an innocent mistake of leaving an S3 bucket exposed or the unwitting oversight of using a default password as login credentials, these types of configuration errors leave the door wide open to security risks.
Take, for instance, the data breach when Deep Root Analytics, a conservative data firm, accidentally exposed 198 million voter records by leaving a cloud storage server unsecured.
In today’s cloud environment, with thousands of resources and new kinds of services introduced almost daily, it is not possible to rely solely on human expertise and manpower to identify and remedy cloud misconfiguration. Any successful security strategy should include technology and processes that automate safeguards to help stem configuration error.
There are security tools available that can scan your cloud environment to establish a baseline. Once the baseline has been established, it is easy to automate remediation of security and policy violations back to that good-known baseline. Just because your infrastructure was once compliant does not mean that it is always compliant. Such tools can also be utilized to enforce security controls that guard against non-compliance. Keeping organizations safe from security risks requires a combination of people, processes, and technology.
To learn more about the human factor in cloud misconfiguration and how cloud professionals view and manage misconfiguration risk, download our complimentary ebook, Cloud Infrastructure Misconfiguration Report.
