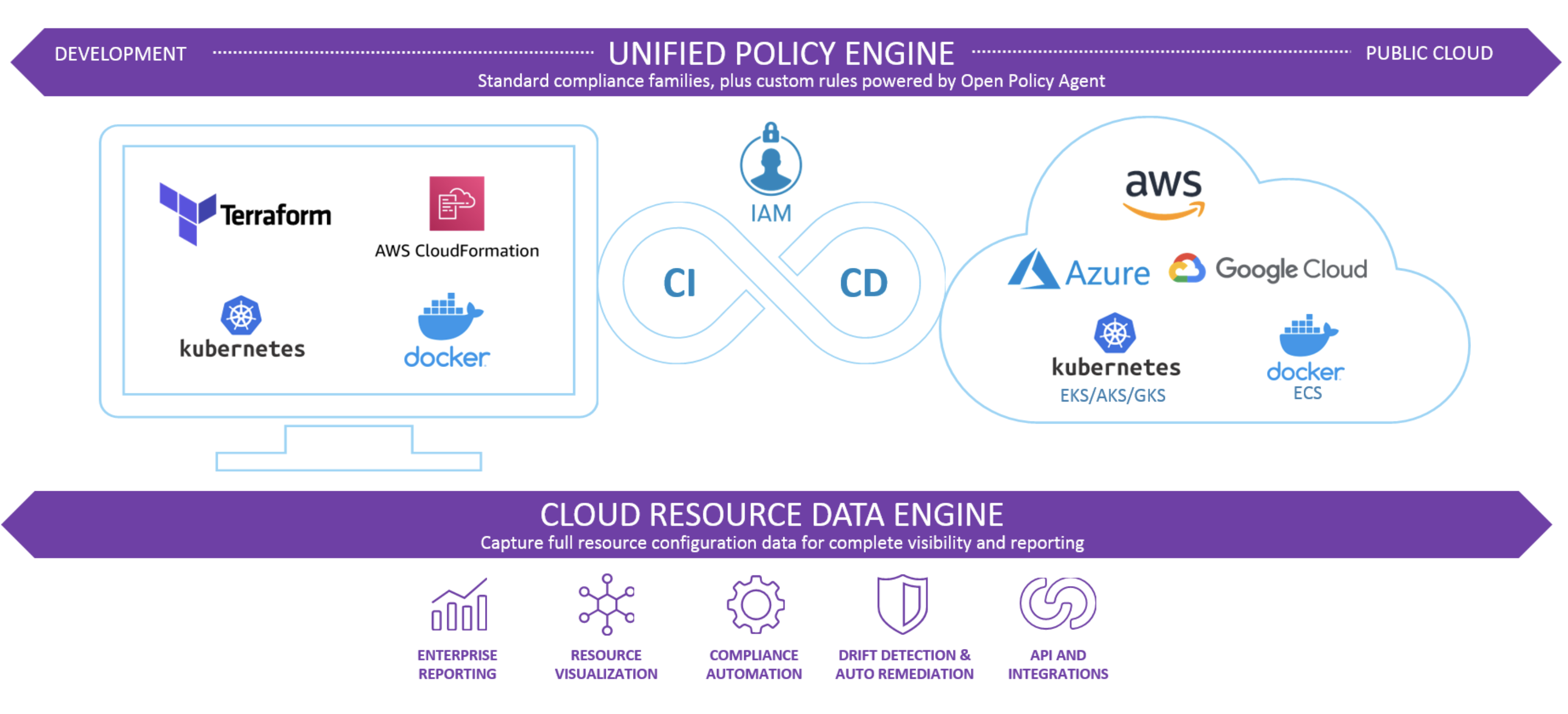
This week, Fugue announced unified infrastructure as code (IaC) and cloud runtime security. For the first time, cloud engineering and security teams can automate security across the development lifecycle using the same policies.
This capability saves cloud teams significant time and ensures consistent policy enforcement that eliminates the security gaps and wasted effort that come with using separate policies to check the security of their IaC and their running cloud infrastructure environment (runtime).
According to Fugue customer Red Ventures, it’s a “game changer.”
Let’s look at how Fugue delivers on this promise.
Fugue IaC: Centralized IaC Security with Open Source Policy as Code
Cloud engineers need tools that help them check that the infrastructure as code templates they’re developing adhere with all applicable industry compliance standards and custom security policies. And the organization needs to ensure their developers are using those tools, and that they’re using the correct policies.
With Fugue IaC, engineers can quickly validate their IaC templates for cloud resources, Kubernetes, and containers against the right policies, and they can build automated IaC checks into Git workflows and CI/CD pipelines to prevent misconfiguration vulnerabilities in deployments. Fugue provides hundreds of pre-built policies mapped to industry compliance families such as SOC 2, NIST 800-53, and PCI out of the box.
Your organization can govern IaC security operations across teams in one place and ensure consistent policy enforcement across the development lifecycle. All cloud stakeholders have full security visibility over policy libraries and IaC code repositories — and they can view tenant-wide IaC-specific security and compliance reports.
Fugue IaC is powered by Open Policy Agent (OPA), the open standard for policy as code. OPA is ideal for infrastructure as code security, and with Fugue you can use it to develop custom rules — including multi-resource checks — using Rego, OPA’s simple and powerful open source language. Developers use Regula, Fugue’s open source implementation of OPA for IaC security, for running IaC checks locally.
OPA and Rego are easy to learn and flexible enough for the most sophisticated enterprise cloud use cases. OPA is a Cloud Native Computing Foundation (CNCF) graduated project.
Tying It All Together: Fugue’s Unified Policy Engine
Establishing effective, efficient, and consistent IaC security is critical to preventing cloud misconfiguration vulnerabilities from reaching the runtime without slowing teams down. But if teams are using a completely different system and set of policies for checking the runtime for security and compliance, things start to fall apart.
There’s multiple tools and policies to manage and maintain. Policies don’t agree. Prioritizing and remediating issues takes a lot longer. Critical vulnerabilities can slip through the cracks.
At Fugue, we believe teams should be able to use the same policies to govern their cloud environment at every stage of the development lifecycle, from IaC to runtime. Fugue’s Unified Policy Engine empowers security teams that are tasked with keeping the cloud runtime secure to use the same policies that engineers developing secure IaC are using.
With Fugue’s Resource Data Engine, which continuously snapshots your cloud environment, including every resource, relationship, configuration attribute, and change over time, teams can also catch misconfigured cloud resources that were deployed outside of IaC and CI/CD pipelines.
For the first time, all cloud stakeholders (developers, operations, security, compliance) are operating efficiently under a single source of truth for cloud security and compliance policy.

