However, in some DevOps environments, security is often neglected or avoided because of the perception that the security team will introduce inefficiencies and dramatically slow the pace of development. Bypass the unnecessary risks of this approach by integrating security directly into your DevOps pipeline.
DevSecOps Provides Agile Security
DevSecOps is established by placing security controls in every phase of your pipeline. Common best practices include:
- Training: Educate engineers to incorporate security best practices into code such as always validating inputs from untrusted data sources or enforcing the principle of least privilege
- Access Control: Limit permission for code commits to qualified developers
- Infrastructure: Create application infrastructure from pre-constructed templates using verified AMIs and containers
- Continuous Integration: After code is committed to version control, statically analyze code for vulnerabilities like buffer overflows or the unwanted inclusion of keys or passwords
- Infrastructure: Verify that logging and monitoring are always enabled
- Continuous Deploy: After deployments are complete, run risk or vulnerability assessment tools on applications and infrastructure
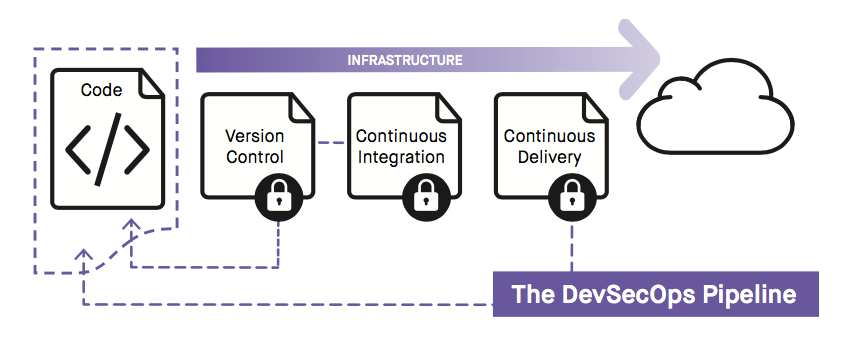
Fugue Integrates Security into DevOps Pipeline
Fugue enforces security controls for the infrastructure components of your CI/CD pipeline. It identifies risks in your cloud infrastructure and ensures they are never repeated. Other benefits to Fugue include:
- Enforce Accredited Templates: Fugue protects infrastructure by making sure that only verified AMIs or containers can be deployed into the cloud. If any other AMIs or containers are used Fugue generates an error before provisioning.
- Identify Policy Violations: Fugue can enforce security controls based on regulatory standards such as NIST 800-53, HIPAA, CIS, or any unique internal security policies. Fugue generates errors when it detects policy violations such as not enabling encryption or logging. Fugue can analyze infrastructure for violations at two stages, when it is initially provisioned, or after application code is deployed.
- Eliminate Configuration Drift: Fugue also detects inadvertent changes to infrastructure, such as mistakenly opening an SSH port on production servers. Fugue automatically restores infrastructure to its known good state, saving both time and resources to prevent security violations.
- Access Management: Fugue uses Role-based Access Control (RBAC) to ensure that only authorized users are permitted to commit code. RBAC provides account and user management for permissions across groups/roles/levels for any complexity of resources. Fugue logs all actions, including RBAC, for accountability.
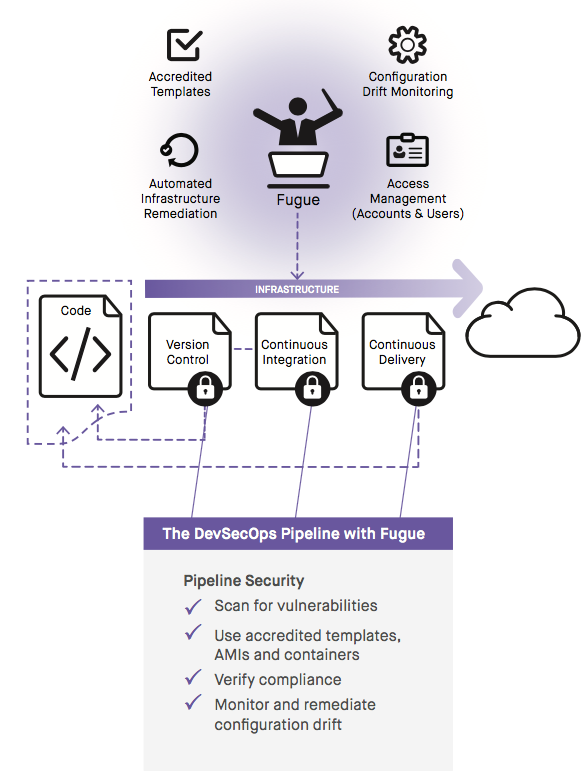
DevSecOps with Fugue
Smart, successful DevSecOps revolves around adding security controls throughout your CI/CD pipeline. Fugue enables you to do this for the infrastructure components of your pipeline, enforcing compliant infrastructure for all your applications.
In short, Fugue provides:
- Easy API-driven integration with common CI/CD tools
- Infrastructure & policy as code (for compliance and internal security policies)
- Automated remediation for all security violations
- A single tool to access, trace, and manage accounts, users, & configurations
Learn more about how Fugue can help your organization move fast and safely in the cloud here.
