When it comes to cloud infrastructure security, two trends emerged in a big way in 2019: headline-producing cloud-native exploits, and the developer movement to address these threats using secure engineering approaches.
We blogged about quite a bit this year, but our top posts clearly reveal two rising trends:
Trend #1: Advanced cloud-native exploits are on the rise
2019 was the year that cloud infrastructure exploits graduated beyond simple misconfiguration attacks to much more advanced ones, often involving bad actors leveraging Identity and Access Management (IAM) services to move laterally in cloud environments and access sensitive data. This isn’t to say organizations are no longer falling victim to their own simple mistakes like making a sensitive S3 bucket publicly accessible (they are), but malicious actors are now employing more sophisticated techniques.
Trend #2: Engineers are empowering themselves to prevent cloud-native exploits
In the cloud, developers are increasingly building their own infrastructure (with infrastructure as code) and they’re taking ownership over ensuring that infrastructure is designed and configured securely--and stays that way (with policy as code). Preventing cloud misconfiguration is far more effective than detecting threats, and tools like Open Policy Agent, the Rego policy language, and Fregot developer tools are empowering engineers to keep their cloud infrastructure secure.
Okay. Starting from the top, here’s a rundown of our top posts of 2019.
Post #1: A Technical Analysis of the Capital One Cloud Breach
Based on publicly-available information about how this attack went down, Fugue co-founder and CTO Josh Stella went about recreating it in his own test AWS environment. The results exposed new cloud misconfiguration vulnerabilities that exist in probably every enterprise cloud environment. These misconfigurations won't likely be flagged by any compliance standard, and security teams won’t likely recognize them as vulnerabilities. Read it here.
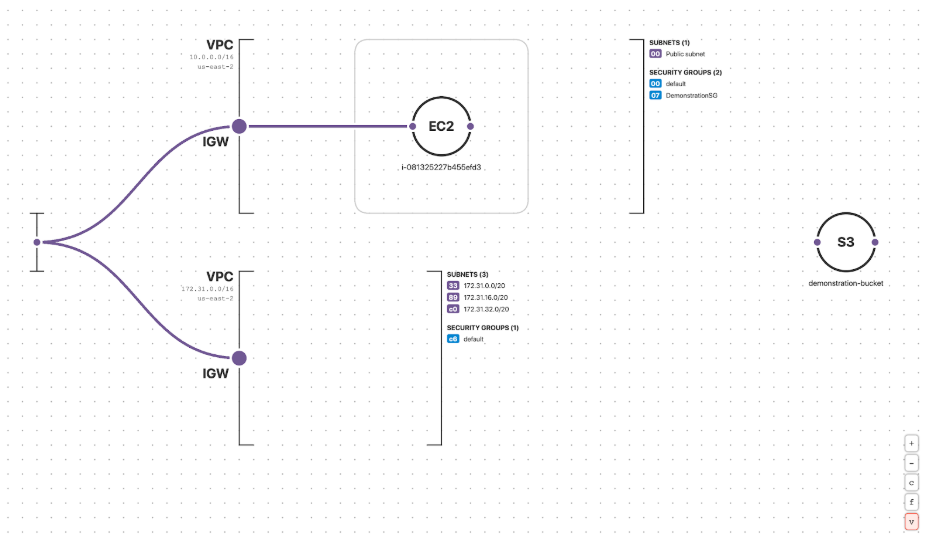
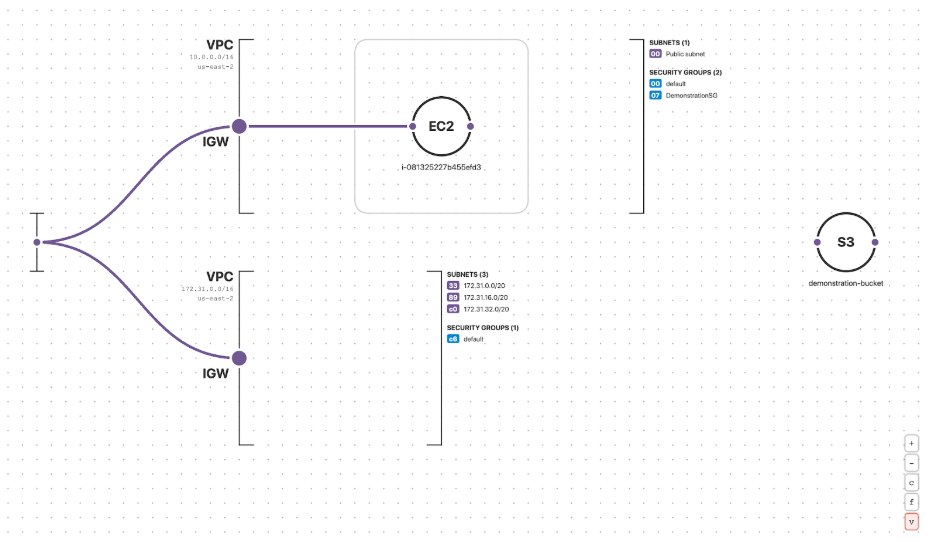
The simulated cloud environment dynamically visualized in Fugue.
See also: Fugue Webinar: Simulating IAM Misconfiguration Attacks
Post #2: Cloud Network Security 101: AWS VPC Endpoints
Getting network security right is critical to operating safely in the cloud, and these blog posts are designed to help developers understand the security posture of cloud-based network services. There are many different ways you can secure your network, but the best approach is to layer multiple methods. The more layers implemented in your security, the harder it is for malicious actors to access your network. In her blog series, Fugue’s Becki Lee focuses on several “layers” of practicing defense in depth.
See also: Cloud Network Security 101: AWS Security Groups vs NACLs
Post #3: Shifting Left on Cloud Security and Compliance
The movement to “shift left” on security and compliance is one largely driven by developers who want to move faster and discover issues earlier in the software development life cycle (SDLC). While most of that effort has been focused on application security, 2019 saw a big uptick in “shifting left” on cloud infrastructure security as well. In this series, Josh Stella looks at how to think about “shift left” for cloud infrastructure security in each phase of the SDLC.
See also: Webinar: Shifting Left on Cloud Infrastructure Security and Compliance
Post #4: Fugue Developer: Free Cloud Security and Visualization for Engineers
Just ahead of AWS re:Invent 2019, we announced Fugue Developer, a free tier designed for individual engineers to build and maintain secure cloud infrastructure in highly dynamic and regulated cloud environments. Fugue Developer provides tools to visualize cloud infrastructure environments, detect resource misconfiguration and policy violations, report on compliance, and understand infrastructure change. It takes just minutes to fully visualize your cloud environment and validate it against policy. Get started with Fugue Developer here.
See also: Webinar: Remediating Cloud Security Issues: Automation Scripts vs. Self-Healing Infrastructure
Post #5: Using Open Policy Agent (OPA) for Cloud Security and Compliance
Just like the challenges of managing large cloud infrastructure operations led to the development of infrastructure as code, ensuring the security and compliance of those environments led to policy as code. Open Policy Agent (OPA) is an open source general-purpose policy engine, and Rego is OPA’s declarative policy language. We’ve been using OPA and Rego at Fugue as the policy-as-code framework in our SaaS solution for cloud security and compliance, and it’s simply amazing. Read on to learn why.
See also: Announcing Fregot: An Open Source Toolkit for Working with Rego and OPA
Thanks to all of you for making 2019 a great year for us here at Fugue. We expect these trends to persist through 2020, so stay tuned as we continue to analyze advanced cloud misconfiguration risks and tools engineers can use to prevent them.
Have a great 2020, everyone!
