Whenever there's talk of the cloud, misconfiguration and the security risk it brings inevitably becomes a part of the conversation. And of course, once you start talking about cloud misconfiguration, “auto-remediation” often creeps into the conversation. But what does “auto-remediation” really mean? The concept of “auto-remediation” is that the solution finds problems or policy violations in your cloud infrastructure and automatically fixes them.
Many cloud security tools now claim to provide “automated” remediation capabilities. There are various approaches to remediation and we wanted to explore three different ones used in tools that are identified as “automated”. Each approach has its advantages and drawbacks, and our objective with this post is to help clarify the capabilities that are available so you can determine which approach is the best fit for your cloud needs.
The three “automated” remediation approaches we examined are:
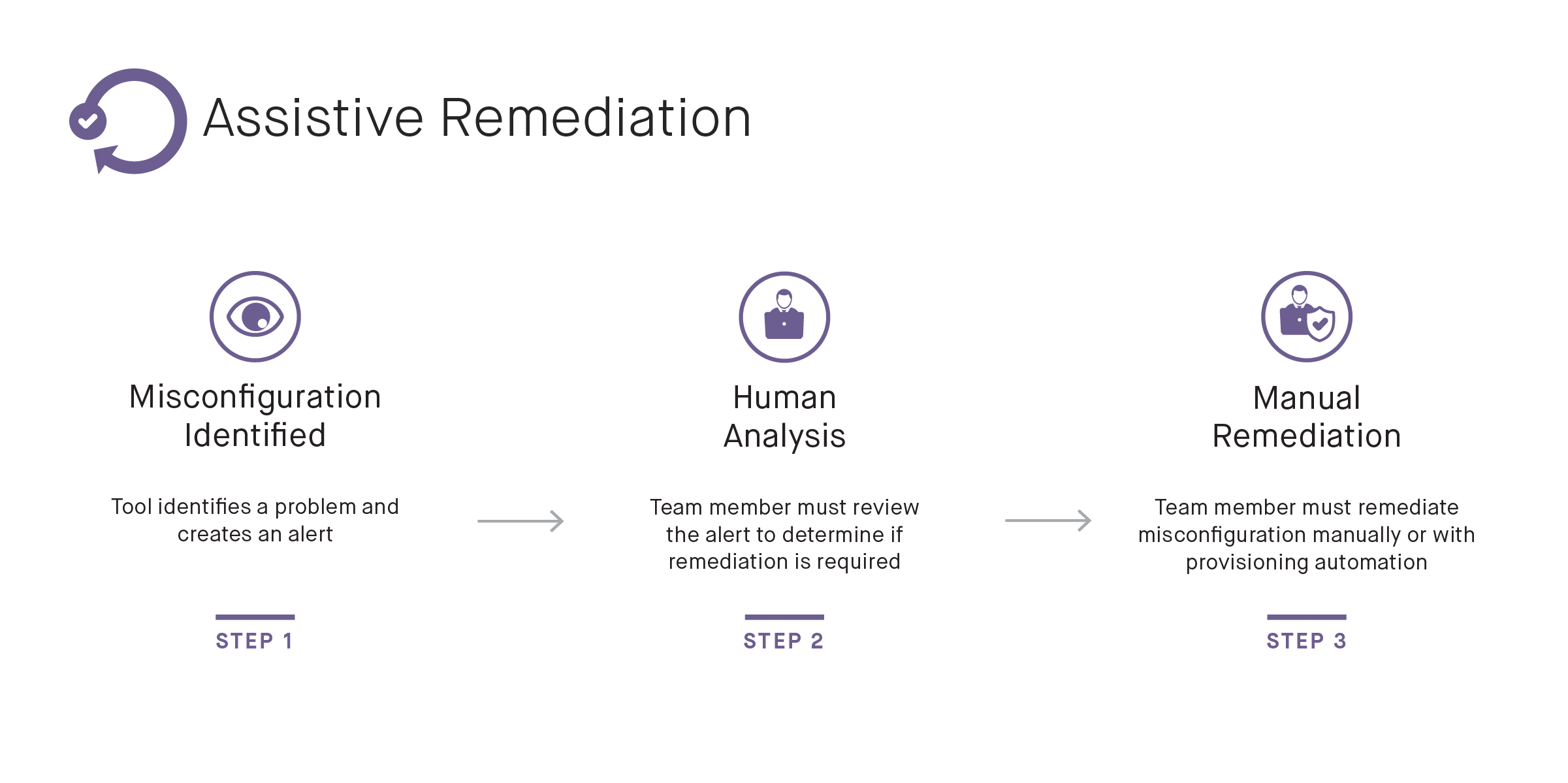
Assistive Remediation
Assistive Remediation is the most common approach. With Assistive Remediation, the tool scans your cloud infrastructure and generates alerts notifying you of problems it has identified. No other action is taken, so this option isn’t specifically “automated” remediation. Instead, it offers explanations and suggestions to help enable DevOps teams to identify and remediate critical misconfiguration events faster. As a tradeoff, the lack of automated remediation means that the tool only needs “read only” permissions to your infrastructure. This can be an ideal option for new cloud users, for security and compliance teams seeking an assessment of their cloud security posture, or for those situations where there’s concern that automating changes will result in bad changes due to false positives.
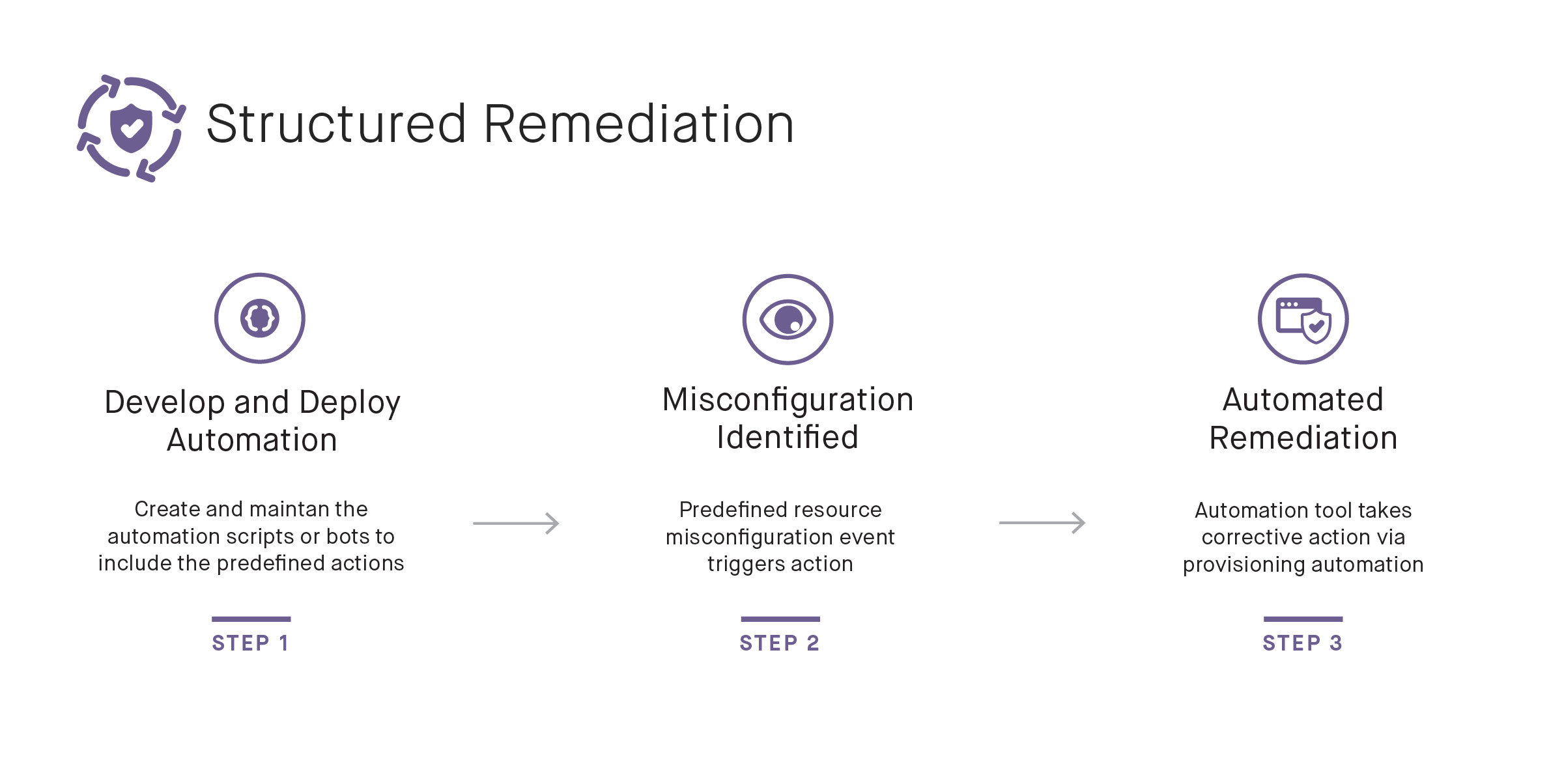
Structured Response
Structured Response adds additional capabilities upon the Assistive Remediation model. In this scenario, the tool provides rules to define a problem along with a structured response to correct the problem. For example, if an AWS S3 bucket is open to the world in violation of your rules, the system will notify you and it will then call an external function to alter the permissions on the bucket.
The benefit of this approach is that it allows for faster response times with a robust audit trail. Having a combination of well-articulated rules and structured responses is an excellent way to show proof of compliance for specific resource configurations.
The tradeoff with the Structured Response approach is that scalability becomes a challenge. Each enterprise must maintain its own set of external functions, and the number can grow fairly quickly as multiple teams may need to slightly customize each function for their own needs. Also, a structured response is only as good as your rulesets, so they must be sufficiently thorough and constantly updated.
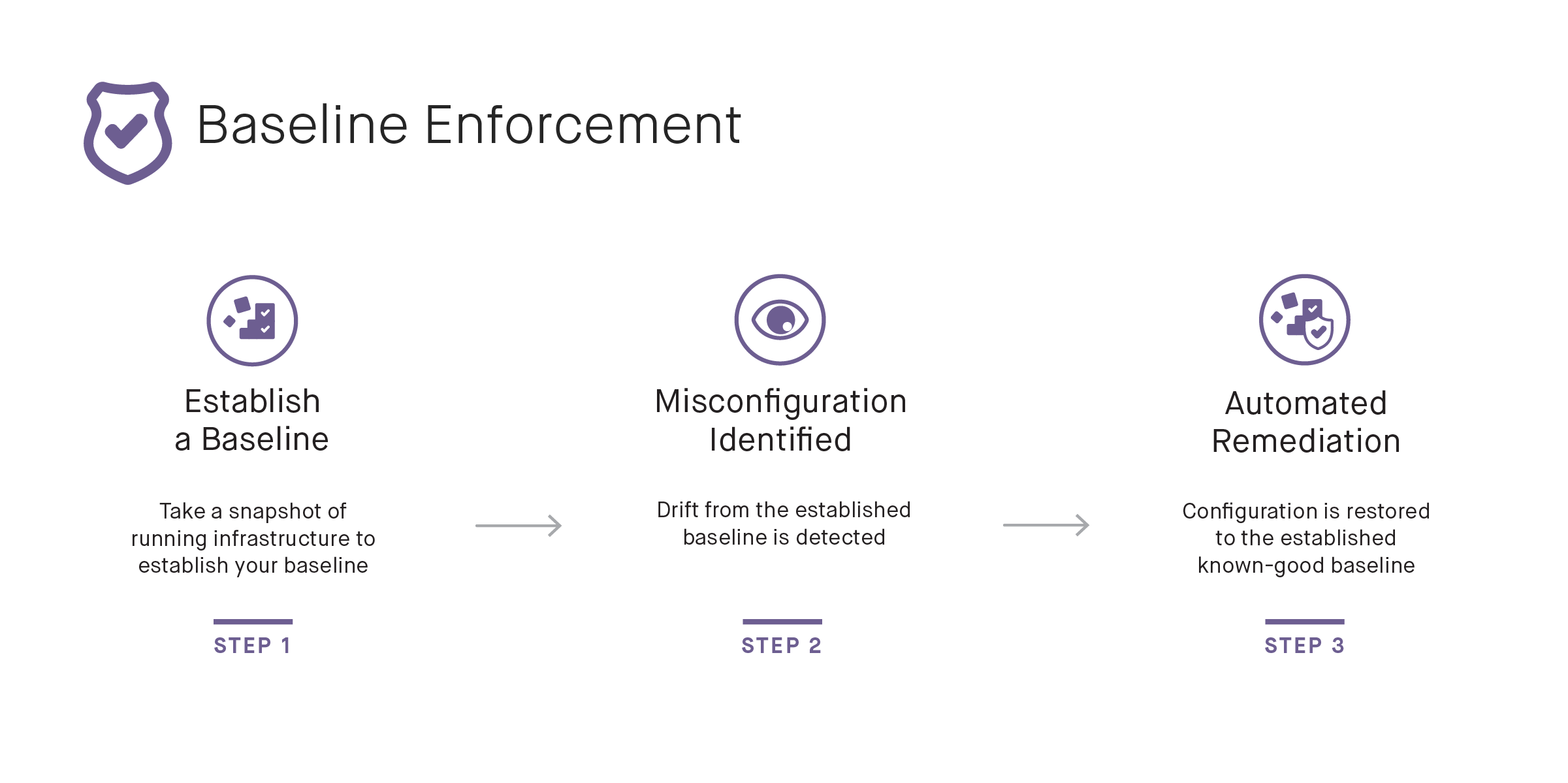
Baseline Enforcement
Baseline Enforcement is the most comprehensive of the three approaches. Similar to the Structured Response approach, if a problem is identified, an alert is generated, and the problem is fixed without the need of human intervention. With this approach, all changes are identified. This includes changes that extend beyond those that have to be explicitly defined for the tool to take action, as found in the Structured Response approach.
Instead of implementing a predefined action based on the identified problem, the Baseline Enforcement approach simply reverts unauthorized changes and restores the infrastructure back to a known-good state. This approach is also more scalable than Structured Response because there’s no need to build and maintain separate automation scripts.
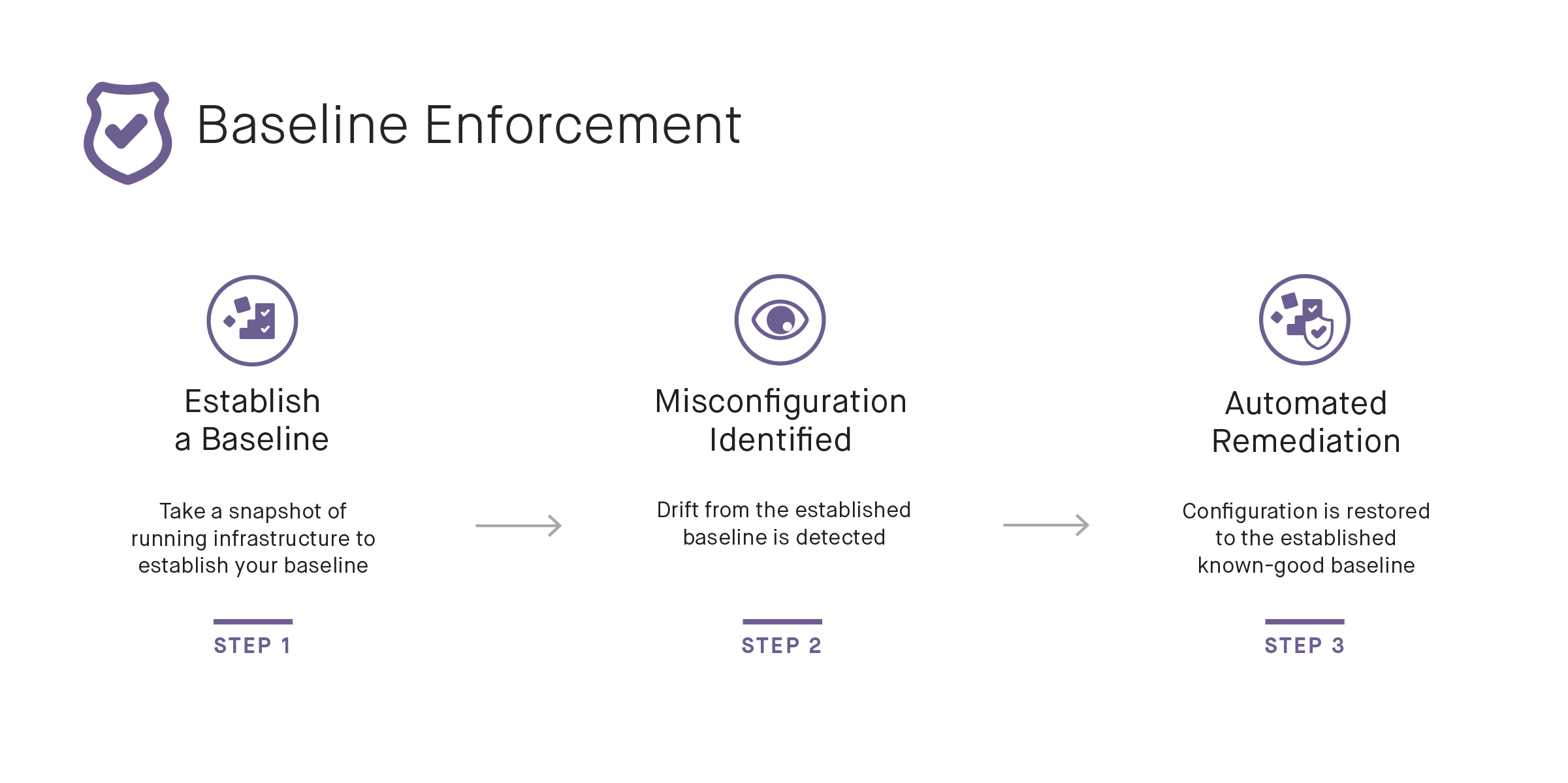
This approach does require the users to first establish a baseline of their cloud infrastructure. For this, users need to have the capability to scan their cloud environment, identify violations and risks, and then correct those violations to establish a solid baseline. Once that baseline is established, the tool can then automatically enforce the baseline and restore the infrastructure back to the known-good state.
Each organization will have different needs for their cloud deployments. For some, alerts and Assistive Remediation is an appealing solution. For others, where mission critical components need to be locked down to protect critical data, the Baseline Enforcement approach is the best fit.
Fugue’s automated remediation incorporates the baseline enforcement approach where all unauthorized changes are automatically reverted back to a good-known baseline. To learn more about how Fugue’s automated remediation works, check out our product.
